Implementing FedRAMP POAM workflow
Learn about the FedRAMP POAM workflow in this section, which includes automation using two distinct robots:
-
Security Scan Automation robot Ingests vulnerabilities from external scan tools, such as Tenable, Rapid7, and Qualys.
-
SAR Vulnerabilities Automation robotImports vulnerabilities identified in annual Security Assessment Reports (SARs).
Each robot has a unique configuration process and contributes to building a complete POAM inventory. The following sections describe how to configure each robot.
What is POAM?
Plan of Action and Milestones (POAM) is a required, regulated report that cloud service providers (CSPs) submit monthly as part of the FedRAMP authorization process. The report documents all cybersecurity vulnerabilities identified within a CSP’s FedRAMP authorization boundary. It also outlines remediation plans, progress updates, and milestone targets for resolving those vulnerabilities. This continuous reporting provides government reviewers with visibility into the CSP’s security status and risk management activities.
Each POAM record typically includes 25 to 30 attributes for every vulnerability. These attributes may include the weakness name and description, source identifier, impacted asset, status, planned remediation steps, milestone dates, and responsible parties. The POAM functions as a compliance artifact and as an operational tracking tool. Rather than serving as a one-time submission, it remains a living document that CSPs update regularly.
Roles and prerequisites for POAM
-
Subscription to the IT Compliance – Federal Contracting Compliance Toolkit bundle.
-
Administrator privileges to Projects, Results, and Robots apps. Obtain the relevant FedRAMP baseline controls as needed.
Where do I implement POAM
You can implement the POAM workflow using Robots, Projects, Result Collection, and Questionnaires apps in Diligent One.
-
Robots automate the ingestion and normalization of vulnerability data from external security scans. They populate the POAM Inventory with structured vulnerability records and import findings from Security Assessment Reports (SAR) linked to specific FedRAMP controls.
-
Projects serve as the primary workspace for configuring FedRAMP programs in Diligent One. POAM vulnerabilities identified in annual assessments (SARs) are documented within FedRAMP projects and linked to the appropriate controls.
-
Results host the POAM Inventory in the form of a Result Collection. Its structure aligns with the FedRAMP POAM Excel template and supports more than 30 attributes.
-
Questionnaires enable security teams to manually enter and complete vulnerability records with details that aren't captured through scan data, including milestones, remediation actions, vendor dependencies, rationale, and adjustments.
-
Impact Report exports the POAM Inventory into the official FedRAMP POAM Excel template. It pulls normalized and enriched data directly from the Results Collection.
Note
The Impact Report feature isn’t included in the default toolkit installation. To enable and configure this reporting export within your environment, coordinate with the Professional Services team.
Steps
Security Scan Automation robot
1. Map configuration
Each security scanner generates a CSV file that lists identified vulnerabilities. These files vary in structure depending on the scanner used. To ensure accurate integration with the FedRAMP Plan of Action and Milestones (POAM) report, it’s important to understand how the scanner’s output maps to the required POAM fields.
To support this integration, a mapping key must be created for each security scanner. If the CSV format remains consistent, this mapping key only needs to be created once per scanner and can be reused with future CSV files from the same source.
Because each scanner outputs data differently, reviewing the CSV file is essential to determine how each column aligns with the corresponding POAM field. The mapping key must be a CSV file that follows a three-column format:
-
Column A POAM report attributes (for example, weakness name, detection date).
-
Column B Corresponding column names from the security scan CSV.
-
Column C Required attributes (Yes or No) to determine uniqueness and inclusion criteria.
This column plays a critical role in determining whether a vulnerability record is unique and should be included in the POAM Inventory. Marking an attribute as Yes indicates that it is required for identifying uniqueness and avoiding duplication during automated ingestion.
-
The Security Scan Automation robot uses the attributes marked Yes to compare incoming vulnerability records against existing entries in the POAM inventory. This comparison prevents duplicate records from being added.
-
At least one attribute must be marked Yes to enable the robot to perform uniqueness checks. Without this requirement, the robot cannot determine whether a vulnerability is new or already present.
For example, if the CVE ID is marked as required, the robot will check whether the CVE already exists in the POAM Inventory. If it does, the record is skipped; if not, it is added.
-
You can mark multiple attributes as required to define uniqueness using a combination of fields.
For example, if you want to report the same CVE for different assets, you can mark both CVE and Asset Identifier as required. This allows the robot to treat each CVE-Asset pair as a distinct vulnerability.
-
Labeling at least one attribute as required is mandatory for the Security Scan robot to function correctly and ensure accurate, deduplicated vulnerability tracking.
-
2. Upload security scan data and configure robot task
Upload the mapping key CSV and security scan file to the Working data tab of the Security Scan Automation robot and provide the following parameters in the Tasks tab:
| Parameter | Detail |
|---|---|
| Security Scan Mapping File | The name of the mapping file uploaded to the Working data tab of the robot. |
| Security Scan File | The name of the security scan file uploaded to the Working data tab of the robot. |
| Weakness Detector Source | The security scanner that produced the CSV file, for example, Tenable. |
Note
A separate robot task is created for each scan type, such as Tenable or Twistlock, with parameters configured to match the specific requirements of that scanner and maintain clarity, avoid overwriting parameters, and support parallel processing.
3. Run the Security Scan Automation Robot
After the parameters are added, you can manually run the robot within the Robots app. The robot ensures to:
-
Parse the scan file using the mapping key.
-
Normalize and import vulnerabilities into the POAM Inventory.
-
Avoid duplicates using required attribute combinations.
-
Flag previously closed vulnerabilities that reappear in new scans.
4. Review records in POAM Inventory
After the robot runs successfully, the security teams access the POAM Inventory in the Results app to review the records. The completion of a POAM record typically requires combining information from three distinct sources throughout a normal workflow:
- Approximately one-third of the attributes are populated automatically through the security scans using the FedRAMP Security Scan Automation robot. The examples include Weakness Name, Weakness Description, asset identifier, original risk rating, and similar fields. These fields are automatically populated based on scan outputs and mapped to required POAM fields.
-
Another third is completed manually using the structured questionnaire, which is assigned to internal resources such as engineering teams responsible for remediation. These teams provide critical remediation details such as Planned Milestones, Overall Remediation Plan, Resources Required, Responsible Party, and other specifics needed for full completion of the POAM report. For more information, see Distributing questionnaires.
For instance, when the POAM specialist identifies a vulnerability, they assign the questionnaire to the appropriate team, who then complete the questionnaire to supply the necessary remediation context.
-
The remaining columns related to deviation requests, which only need to be filled out in specific cases. Deviation attributes apply when the Cloud Service Provider (CSP) requests FedRAMP to consider extending the Service Level Agreement (SLA). For example, they can justify that a vulnerability is less risky than the scan suggested or is a false positive. These columns include Operational Requirement, Deviation Rationale, Supporting Documents, Vendor Dependency, Last Vendor Check-in Date, Vendor Dependent Product Name, Adjusted Risk Rating, and False Positive. If the CSP is not pursuing a later due date or risk adjustment, these fields will typically remain blank until export.
This review step ensures that each POAM record is complete, accurate, and aligned with FedRAMP reporting requirements through automation, manual input, or a conditional deviation approach.
5. Customize your view of POAM records in Results
You can personalize your view of POAM records in the Results app by using built-in customization features such as conditional formatting, color-coding, column reordering, and column visibility settings. These options allow you to highlight priority vulnerabilities, bring frequently used fields to the forefront, and hide less relevant data to reduce visual clutter. Additionally, you can use reporting visuals to track trends and remediation progress and add interpretations to annotate records with context or rationale. These capabilities help streamline vulnerability management and support more effective reporting and decision-making. For more information, see Viewing table data.
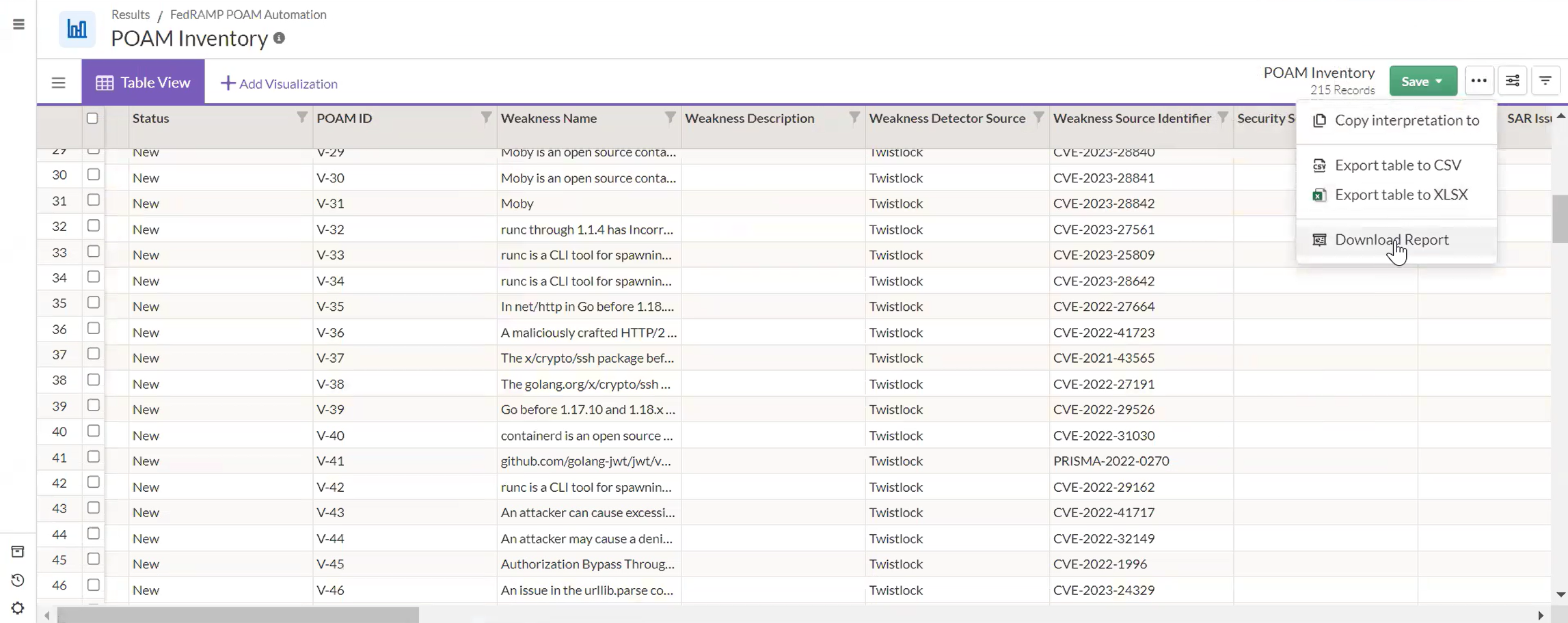
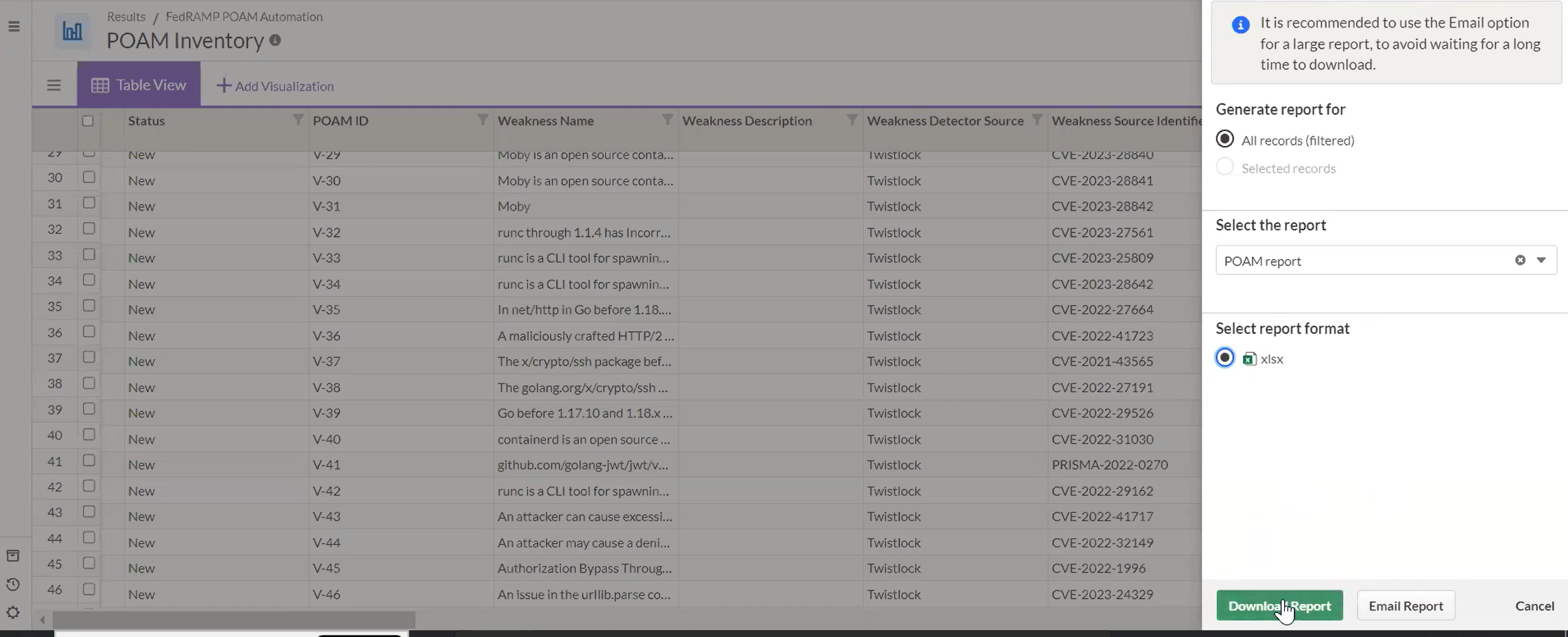
6. Export records to POAM report
After completing all records and reviewing their statuses, the Impact Report feature is used to export the POAM Inventory into the FedRAMP POAM Excel template. The export automatically sorts open and closed vulnerabilities according to FedRAMP requirements.
Optional filters or record selections allow customization of the export, supporting multiple authorization boundaries or tailored reporting needs.
SAR Vulnerabilities Automation robot
Configure SAR Vulnerabilities Automation robot
The SAR Vulnerabilities Automation Robot imports findings from annual Security Assessment Reports (SARs) and maps them to relevant FedRAMP controls.
-
Access the robot from the Robots app and upload the SAR findings file to the Working Data tab.
-
Configure the robot task with the SAR file name and project ID.
-
The robot parses the SAR content and populates the POAM Inventory in the Results app.
-
Review and complete the imported records using questionnaires and link them to appropriate controls.
These records are tagged as SAR-sourced and linked to specific controls for traceability.
POAM OSCAL robot
The POAM OSCAL robot is part of the FedRAMP Reporting Toolkit. It converts the structured vulnerability data from the POAM Inventory (in the Results app) into a machine-readable OSCAL (Open Security Controls Assessment Language) format, as required by FedRAMP and NIST.
1. Prepare the POAM Inventory
Preparing the POAM Inventory involves ensuring that all vulnerability records in the POAM Results Collection are complete and current. You must ensure that the required fields, such as weakness name, detection date, remediation steps, and milestones, are populated. You can also review and complete records using questionnaires if additional information is needed.
2. Access POAM OSCAL robot
Access the Robots app in Diligent One and locate the POAM OSCAL Export Robot, which is part of the FedRAMP Reporting Toolkit.
3. Upload required files
In the Working Data tab, you upload any required configuration files or templates. Some versions may not require a template. You must also ensure that the POAM Inventory is correctly linked to the robot to support accurate data processing.
4. Configure robot parameters
In the Tasks tab, you configure the robot by providing the following parameters:
-
Project ID Identifies the FedRAMP project associated with the POAM data.
-
API Token Authenticates access using your Diligent One HCL token.
-
Any additional parameters that reflect your environment or export preferences.
5. Run the robot
Start the export process by triggering the robot. During execution, the robot performs the following actions:
-
Extracts data from the POAM Inventory.
-
Converts the data into a valid OSCAL JSON file.
-
Validates the file structure against the OSCAL schema.
6. Download the output
After the task completes, you can view the output by navigating to Task Run Details. The system generates an OSCAL POAM JSON file, which you can download. This file meets the requirements for FedRAMP submission and can also be used for further validation.