Implementing enterprise risk management
Assessment of different types of risks is often managed with disparate processes in separate parts of the organization. To be effective, the ERM function needs to understand the different levels of risk that have an impact on all areas of an organization, and the techniques being used to reduce risk. In this article, we discuss how to implement enterprise risk management using the Strategy and Projects apps.
This article builds on the examples illustrated in Identifying strategic objectives and risks.
What does it mean to implement enterprise risk management?
Implementing enterprise risk management is a continuous and evolving process that ensures an organization is aware of current and emerging risks that could alter expected outcomes, and is able to proactively respond to risks.
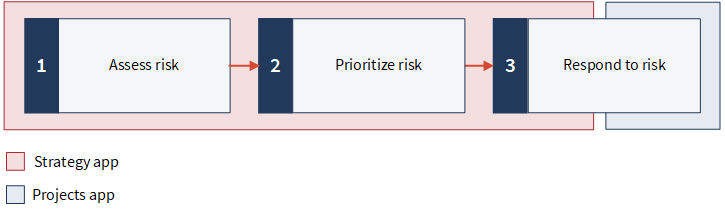
There are three key processes involved in implementing ERM:
- Assessing risk involves developing a common set of assessment criteria that can be used across operating segments, entities, or business units, and determining how much risk an organization faces
- Prioritizing risk involves comparing the level of risk against pre-determined target risk levels and tolerance thresholds
- Responding to risk involves examining response options, performing cost-benefit analyses, formulating response strategies, and developing risk response plans
Where do I implement enterprise risk management?
At Diligent, we use the Strategy and Projects app to assess, prioritize, and respond to risk. Our ERM program enables us to align on our values, vision, and valuation, accelerate our growth agenda in our go-to-market capability and product innovation, and ensure we always deliver the best experience to our customers.
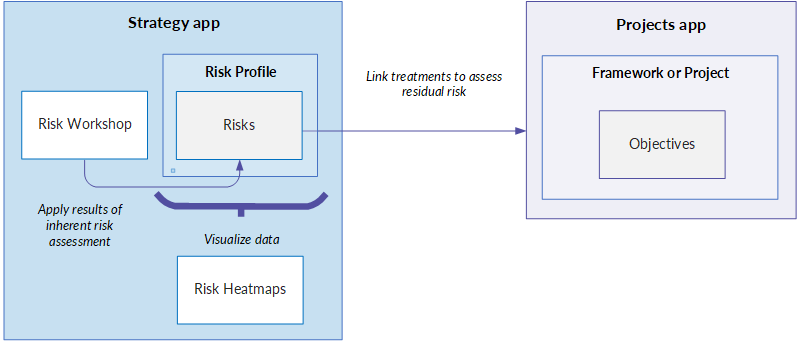
The big picture
- Risk Workshops can be used to collaboratively assess inherent risk within an organization, and the results can be applied to your organizational risk profile.
- Once the inherent risk assessment is complete, you can visualize risk using configurable Risk Heatmaps, and define risk Treatments by linking Objectives (contained in Frameworks and Projects) with strategic risks.
Once you have finished your inherent risk assessment and preliminary treatment evaluation, you can assess residual risk, and better understand the areas of the organization that are of most concern.
Steps
Ready for a tour?
Let's take a closer look at these features in context.
1. Assess risk
Assessing risk is a process in enterprise risk management that involves determining how much risk an organization faces. Many organizations begin by qualitatively assessing risk first and then develop quantitative capabilities over time to align with their decision-making requirements.
Develop risk assessment criteria
The first step is to develop a common set of assessment criteria that can be used across operating segments, entities, or business units. This allows you to perform diverse risk scoring, assess risk on multiple factors, and specify a risk assessment model that is used for your industry-specific risk framework.
Example
Scenario
You are a risk professional that needs to logically assess risk across your organization. Since your organization is new to enterprise risk management, you want to begin by assessing risk in terms of likelihood and impact. By configuring the way risks are scored, you can model your organizational risk framework, and apply the framework to all identified risks.
Process
Help topic Configuring risk scoring settings
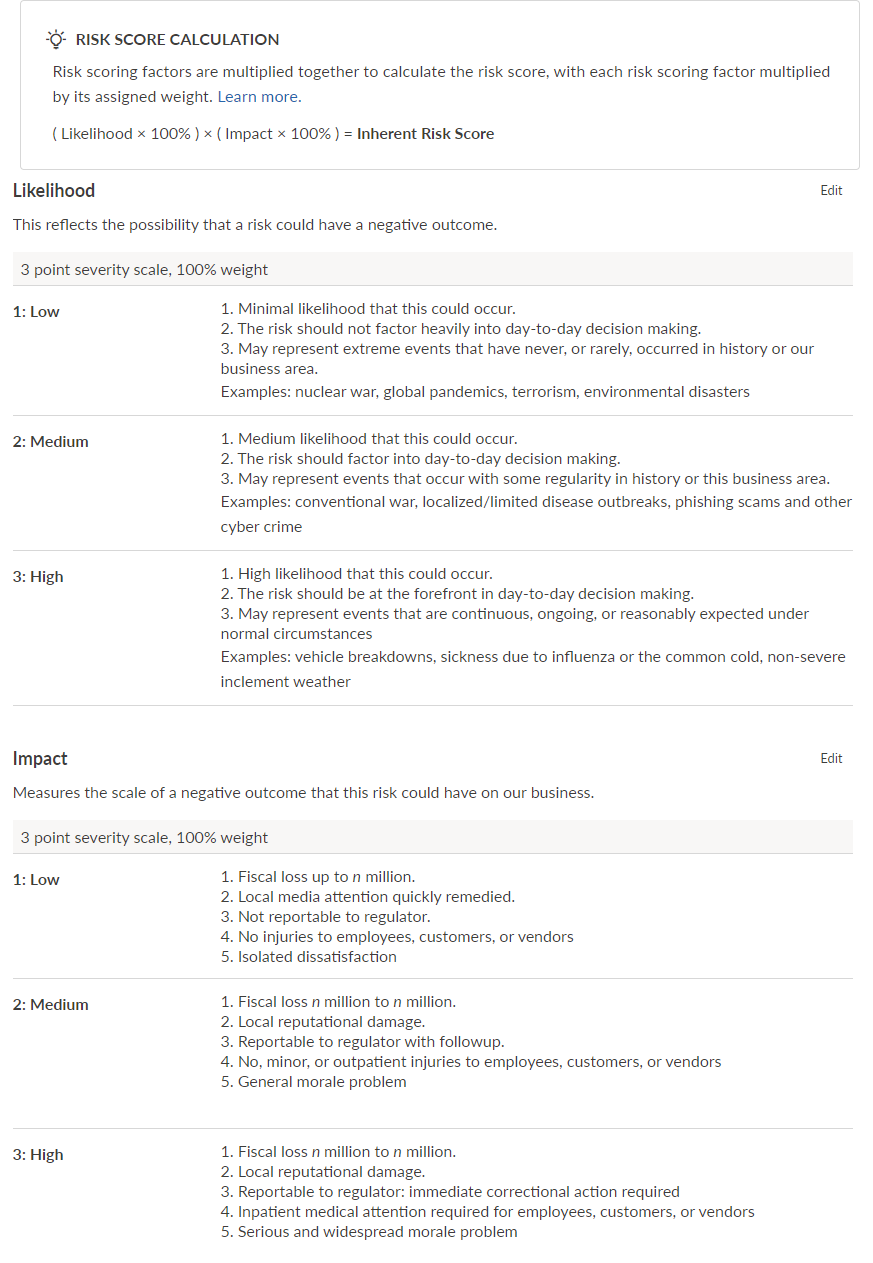
You navigate to Scoring section within Settings in Strategy, and develop the following risk scoring criteria:
- Likelihood (3-point scale: 1-Low, 2-Medium, 3-High)
- Impact (3-point scale: 1-Low, 2-Medium, 3-High)
You also specify the weight of each risk scoring factor as 100% to reflect the equal importance of both impact and likelihood.
Result
All risks across your organization can now be assessed by likelihood and impact, using a 3-point scale:
Assess inherent risk
Inherent risk is a calculation that derives from an assessment of an untreated risk – or the raw risk an organization faces if no controls or other mitigating factors have been put in place. Assessing inherent risk involves associating risks with strategic objectives defined in the Strategy Map, and assessing risk across all operating segments on multiple risk scoring factors. Once you specify scores, Strategy automatically calculates the inherent risk.
Tip
To avoid manually scoring strategic risks, you can use Assessment Drivers to automate different risk assessments. You can link a metric created in the Results app to a risk assessment in Strategy in order to inform the assessment, and auto-populate inherent risk scores based on pre-defined metric ranges. Key stakeholders can be notified when changes to the risk assessment occur.
Example
Scenario
Now that you have set up your organization's risk assessment criteria, you can begin assessing inherent risk – the risk that exists when no controls or other mitigating factors have been put in place. To begin the process, you want to assess the Latex formula risk, which centers around the possibility that the top secret formula could accidentally fall into the hands of competitors. Your organization, Vandelay Industries, would most certainly be out of business if this were to happen.
Process
Help topic Assessing inherent risk
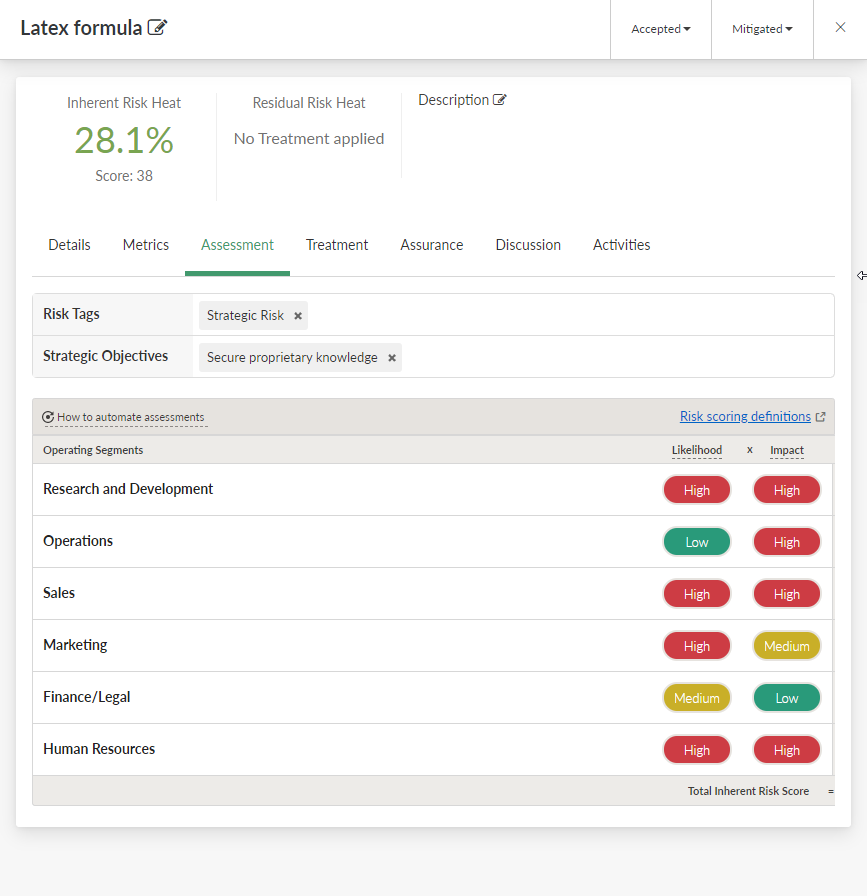
First, you open up the Latex formula risk assessment, and associate the risk with the relevant strategic objectives that the risk threatens. Then, you assess the risk across all relevant departments on based on likelihood and impact.
- Strategic Objectives Innovation-Driven Strategy, International Expansion, Increase Brand Recognition by 25% (Marketing), Double Digit Revenue Growth (Sales), Maintain Category leadership, >35% Net Promoter Score
- Departments Research and Development, Operations, Sales, Marketing, Finance / Legal, Human Resources
Result
You have completed the inherent risk assessment for the Latex formula risk:
Conduct risk workshops
Risk workshops provide a collaborative online forum for gathering additional input and collaboratively assessing risk with executive management and business unit leaders. External consultants that come into an organization can use the risk workshop feature to conveniently manage and integrate input from various stakeholders. Each participant can score risks, and the scores are automatically averaged and aggregated into a single risk assessment that can be applied into a single risk profile view.
Tip
There are some key things you can do to successfully facilitate a risk workshop:
- Provide clear definitions of risk scoring criteria ensure that definitions are available to all participants to provide for a consistent approach to scoring risks. The simplest way to do this is to provide meaningful descriptions in risk scoring factors and individual scores. You can do this while configuring your risk scoring settings. Risk workshop participants will then have access to these definitions while scoring risks.
- Choose the appropriate participants choose people from different departments that know the business well and can provide insight into specific business operations
- Limit the number of participants best practice is to involve 10 - 25 participants; if you need to involve large numbers of participants, sending out a survey from the Results app is a more efficient method
Example
Scenario
You want to invite different stakeholders to collaborate in the risk assessment process, but unfortunately, you cannot get key stakeholders in the same room together at the same time. All of the identified strategic level risks are owned by the Board or C-suite executives, and but these individuals do not have comprehensive knowledge of how individual parts of the business are operating. You need a method of gathering input from various people in the business, and conveniently managing their input in a single, central location.
Process
Help topic Facilitating risk workshops
First, you create a risk workshop and add the risks that participants in the workshop will assess in a collaborative online forum. Then, you add the relevant participants, and send the risk workshop to each participant. After the participants have finished scoring risks, the scores are automatically averaged and aggregated into a single risk assessment, and you decide to apply the aggregated risk assessment to your organizational risk profile.
Result
The inherent risk assessment for all identified risks in the organization is now complete:
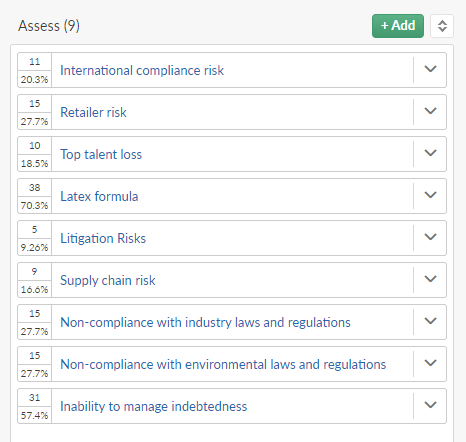
2. Prioritize risk
Risk prioritization is the process of determining risk management priorities by comparing the level of risk against predetermined target risk levels and tolerance thresholds. Risk can be viewed not just in terms of financial impact and probability, but also on the basis of subjective criteria such as health and safety impact, reputational impact, vulnerability, and speed of onset.
Organize risks by state
You can organize risks by assigning each risk to a state and defining its current status in the risk mitigation workflow. Each state is displayed in a separate column within the risk profile. You can move risks from one state to another based on the risk assessment, and your organization's risk tolerance and appetite.
Example
Scenario
Now that each identified risk has been assessed across your organization, you want to organize the risks and assign them different statuses, or states, based on your organization's risk mitigation workflow.
Process
Help topic Assigning a risk to a state
You move risks from one state to another based on the assessment of the risk and the risk tolerance of your organization. For certain risks, you specify a duration of time to accept or transfer the risk. Specifying a time frame will allow you to easily re-assess certain risks at a later date.
Result
Your risk profile is setup as follows:
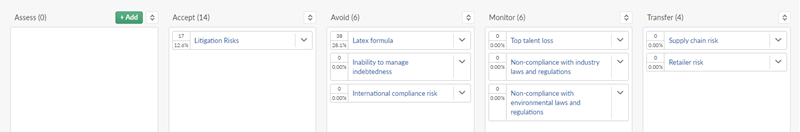
Visualize risks
Visualizing risks helps to establish and communicate a holistic view of risks affecting the organization. Risk Heatmaps are often used to convey the potential likelihood and impact of risks so that strategic decisions can be made for the health of the organization. The Strategy Heatmap can also be used to visualize the aggregation of risk in the organization, and can help to inform decision-making as to where to provide resources to mitigate priority risks.
Example
Scenario
You need to prioritize risk, but you are finding it challenging to compare all of the risks across your entire organization. You recognize that visualizing risk will not only help you present the results of a risk assessment, but also allow you to decide which areas of the organization are of most concern so that you can deploy the appropriate resources, accordingly.
Process
Help topic Understanding risk heatmaps
You open the default Risk Heatmap to determine which risks should be considered as the primary focus. The areas of greater concern are represented in the upper-right quadrant of the risk heatmap, and the areas of lower concern are represented in the lower right quadrant:
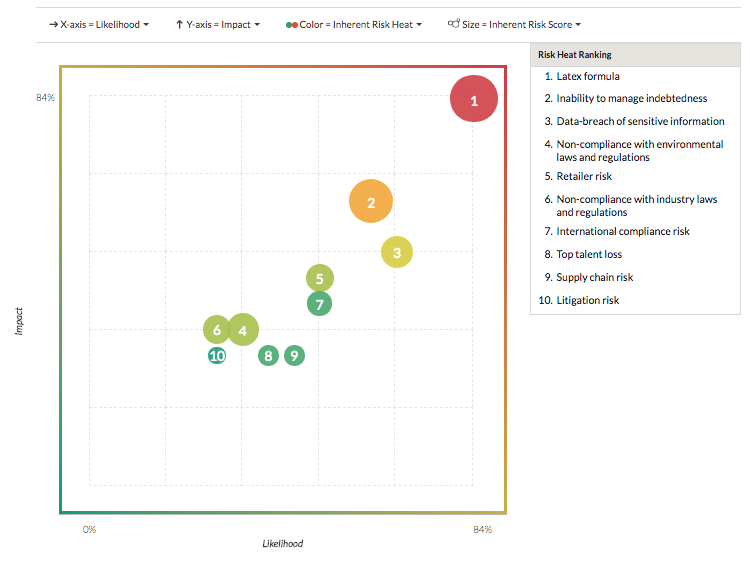
Result
Based on the Risk Heatmap, you are able to quickly determine the most concerning risks for your organization.
3. Respond to risk
After prioritizing risks, it's time to define risk response plans and assess residual risk. The ERM function must be extended by the people in frontline operational positions who are closest to the risks – and this can happen by connecting operational risk and control data from Projects to strategic risks in Strategy. This hybrid top-down and bottom-up approach provides the opportunity to achieve comprehensive coverage of all risks identified in annual assessments, and embeds accountability by leveraging the expertise of the appropriate people in the organization.
Define risk treatments
Risk treatment are the measures an organization takes to mitigate risk. Measures may include initiatives, programs, policies, or control objectives, which you can create in Projects and link to strategic risks in Strategy. The linkage helps you ensure complete coverage of all operational risks identified during annual risk assessments, and allows you to determine how well your organization is doing in mitigating risk.
Tip
Sometimes, the preliminary treatment evaluation may show that you are investing in too many resources to mitigate a risk (Treatment% >= 100%). In this case, the risk assessment shows potential opportunities for reducing the amount of treatment to a particular risk, and scaling back resources associated with the risk treatment.
Example
Scenario
As a result of the risk prioritization process, you have identified that the risk that is of primary concern to your organization is the Latex formula risk. With an inherent risk heat of 70.3%, you know that coordinated efforts need to be made to ensure the risk is mitigated appropriately. You begin working closely with the assurance team to define treatments to reduce the likelihood and impact of the Latex formula being stolen.
Process
Help topic Defining risk treatment
The assurance team creates a Latex Facility Security Review project in the Projects app, and defines the following objective:
Ensure that physical security is properly maintained outside
In Strategy, you open the Latex formula risk, navigate to the Treatment tab, and link the recently created objective in Projects to the Latex formula risk.
Result
A relationship is defined between the strategic risk in Strategy and the linked objective in Projects , allowing you to track assurance and testing results, and assess residual risk.
Assess residual risk
After assessing inherent risk and defining how the risk is being treated, you can perform a preliminary treatment evaluation that assesses how much the treatment reduces the risk. This allows you to identify areas where the business is exposed to risk beyond the organizational risk appetite. Assessing residual risk involves specifying a treatment percentage to define how much of the treatment reduces the inherent risk. The treatment percentage is based on the expected effectiveness of treatment efforts in place, before controls have been tested to provide assurance.
Tip
You can specify a percentage between 0-100%. The total Treatment % can add up to more than 100%. However, an aggregate treatment greater than 100% may indicate that your organization can consider revising the treatment of the risk and reduce costs associated with treating the risk.
Example
Scenario
Now that you have defined the relationship between the Latex formula risk and the physical security objective, you need to perform a preliminary treatment evaluation that assesses how much the treatment reduces the risk. The evaluation will enable you to identify areas where your business is exposed to risk beyond the organization's risk appetite.
Process
Help topic Assessing residual risk
First, you specify a treatment percentage to define how much of the treatment reduces the inherent Latex formula risk. You base the treatment percentage on the expected effectiveness of the treatment efforts in place, before controls have been tested to provide assurance:
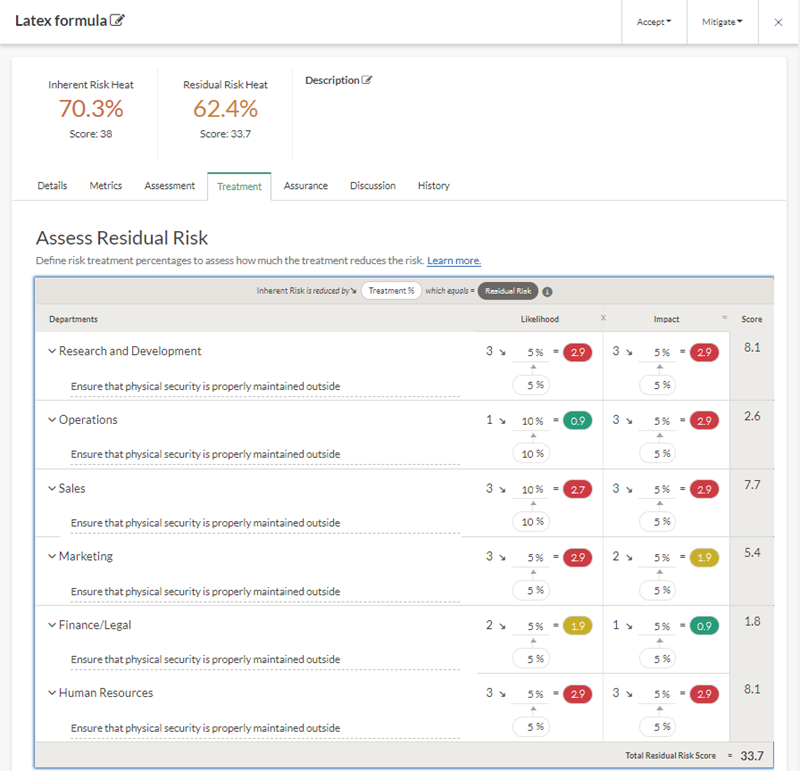
Result
As you enter each percentage, the Treatment % for all treatments associated with an operating segment automatically updates. The Residual Risk Score and Residual Risk Heat values also automatically updates. Based on the results of the residual risk assessment, you can choose to either accept or avoid the risk.
Scope and assess process-level risks and controls
Based on the results of the strategic risk assessment, assurance teams can begin planning and scoping micro-level or process-level risks and controls, and centralizing their workpapers and communications in the Projects app. Each engagement can be planned with background, objectives, and scope that frame the final report, and planning files can be attached, as required. The assurance team can quantify risks using a numeric scale based on the risk framework your organization chooses to follow, assess the effectiveness of controls and note any issues, present quantified data to show how effectively the organization's key controls are mitigating expected operational risks, and assign resources to the areas of highest risk.
Tip
You can integrate evidence from control testing in Projects to aggregate transaction data back to the strategic risk in Strategy, and use the data to backup your recommendations to executive management and board members.
Example
Scenario
As part of treating the Latex formula risk, you need to ensure that the treatment is working – that is, you need assurance that the Latex formula risk is being treated appropriately, and that you are not wasting resources on ineffective procedures that aren't mitigating the risk.
Process
Help topicExecuting procedures and testing controls
To determine the effectiveness of the treatment, the assurance team tests each of the procedures listed under the Ensure that physical security is properly maintained outside objective:
- 3-01 Windows should be constructed from or covered with materials which will provide protection from forced entry. Windows not consisting of these materials should be protected by an Intrusion Detection System. The IDS alerts a response service that responds within 15 minutes.
- 3-02 On weekends, only the main entrances of facilities (South 1 in Denver (DV1)) and South 2 in Los Angeles (LA1)) are to permit key card entry.
- 3-03 Visual monitoring shall be maintained at all times outside of working hours.
- 3-04 The lighting shall be of sufficient intensity to allow detection of unauthorized activity.
The assurance team also weighs each procedure at 25%, meaning that the percentage of the risk that the procedure mitigates is 25%.
Result
The assurance team captures each procedure evaluation, and identifies an issue as a result of executing procedure 3-02.
What's next?
Learn how to report and monitor risks
Using a combination of the Strategy, Projects, and Results apps, you can track assurance and testing results associated with strategic risks, integrate data to help monitor risks, and generate a variety of reports to share with the relevant stakeholders.
To find out more, see Reporting and monitoring risk.
Enroll in an Academy course
Continue to build your knowledge on the concepts introduced in this article by taking the STRAT 100 learning path.
Academy is Diligent's online training resource center. Academy courses are included at no extra cost for any user with a Diligent One subscription. For more information, see Academy.