Connecting to Active Directory
Active Directory is Microsoft's Directory Server that provides a LDAP-compliant database containing objects such as users, groups, and computers. Use Analytics's data connector to import your organization's Active Directory data.
Note
You cannot use this connector independently of Analytics. You can configure a DSN for the connector driver using the Windows ODBC Data Source Administrator, however you must test the DSN connection from within Analytics and not from the connector's Windows DSN configuration dialog.
Before you start
To connect to Active Directory, you must gather the following:
- the domain name or IP address of the Active Directory server
- the correct connection port
- the connecting user account, including the distinguished name of the user and the password
For help gathering the connection prerequisites, contact the Active Directory administrator in your organization. If your administrator cannot help you, you or your administrator should contact Active Directory Support.
Create an Active Directory connection
- From the Analytics main menu, select Import > Database and application.
- From the New Connections tab, in the ACL Connectors section, select Active Directory.
Tip
You can filter the list of available connectors by entering a search string in the Filter connections box. Connectors are listed alphabetically.
- In the Data Connection Settings panel, enter the connection settings and at the bottom of the panel, click Save and Connect.
You can accept the default Connection Name, or enter a new one.
The connection for Active Directory is saved to the Existing Connections tab. In the future, you can reconnect to Active Directory from the saved connection.
Once the connection is established, the Data Access window opens to the Staging Area and you can begin importing data. For help importing data from Active Directory, see Import data using the Data Access window .
Connection settings
Basic settings
| Setting | Description | Example |
|---|---|---|
| User |
The distinguished name of a user. Together with Password, this field is used to authenticate against the Active Directory server. |
MYDOMAIN\test |
| Password |
The password for the distinguished name of the specified user. Together with User, this field is used to authenticate against the Active Directory server. Note You may connect without providing a password if your Active Directory server permits anonymous connections. Based on your server's security configuration, anonymous connections may be able to list available tables. However, such connections may not be able to select data from some or all of the tables listed. For more information about your Active Directory security configuration, contact your organization's administrator. |
|
| Server |
The domain name or IP of the Active Directory server. This does not need to include the LDAP:\\ portion, only the server domain name or IP. |
10.120.1.110 |
| Port |
The port the Active Directory server is running on. The default value is 389. Together with Server, this property is used to specify the Active Directory server. |
389 |
| Base DN |
The base portion of the distinguished name, used for limiting results to specific subtrees. Specifying a base DN may greatly improve performance when returning entries for large servers by limiting the number of entries that need to be examined. |
DC=myConnection,DC=com |
| LDAP Version | The LDAP version used to connect to and communicate with the server. Valid options are 2 and 3 for LDAP versions 2 and 3. | 2 |
| Auth Mechanism |
The authentication mechanism to be used when connecting to the Active Directory server:
|
SIMPLE |
| Scope |
Whether to limit the scope of the search to:
Tip Limiting scope can greatly improve the search performance. |
BaseObject |
Advanced settings
| Setting | Description | Example |
|---|---|---|
| Use Default DC | Used to connect to the default Domain Controller and authenticate using the current user credentials. | false |
| Convert Datetime to GMT |
Converts datetime fields to GMT time zone during import. If false, the datetime value is converted to the operating system time zone of the machine running Analytics. |
true |
| Limit Key Size |
The maximum length of a primary key column. Setting the size to 0 will make the key length revert to the original length. This property makes the connector override the reported length of all the primary key columns. |
255 |
| Map to Long Varchar |
Controls whether or not a column is returned as SQL_LONGVARCHAR. Use this setting to map any column larger than the specified size so they are reported as SQL_LONGVARCHAR instead of SQL_VARCHAR. |
-1 |
| Map to WVarchar |
Controls whether or not string types map to SQL_WVARCHAR instead of SQL_VARCHAR. It is set by default. String columns must be mapped to SQL_WVARCHAR to accommodate various international character sets, so MapToWVarchar is set to true by default. You may set it to false to use SQL_VARCHAR instead. |
true |
| Pseudo Columns |
Indicates whether or not to include pseudo columns as columns to the table. This setting is particularly helpful in Entity Framework, which does not allow you to set a value for a pseudo column unless it is a table column. The value of this connection setting is of the format "Table1=Column1, Table1=Column2, Table2=Column3". You can use the "*" character to include all tables and all columns. |
MyTable=* |
| Upper Case Identifiers | Report all identifiers in uppercase, including table and column names. | false |
| SSL Server Cert |
The certificate to be accepted from the server when connecting using TLS/SSL. You can specify any of the following:
If using a TLS/SSL connection, this property can be used to specify the TLS/SSL certificate to be accepted from the server. Any other certificate that is not trusted by the machine will be rejected. |
C:\cert.cer |
| Support Enhanced SQL |
Enhances SQL functionality beyond what can be supported through the API directly, by enabling in-memory client-side processing:
Note This setting must be false to support filtering using the where clause syntax. Execution of predicatesThe connector determines which of the clauses are supported by the data source and then pushes them to the source to get the smallest superset of rows that would satisfy the query. It then filters the rest of the rows locally. The filter operation is streamed, which enables the driver to filter effectively for even very large datasets. Execution of JoinsThe connector uses various techniques to join in memory. The driver trades off memory utilization against the requirement of reading the same table more than once. Execution of AggregatesThe connector retrieves all rows necessary to process the aggregation in memory. |
false |
Filtering the rows returned
The Active Directory connector uses an SQL filtering syntax that aligns closely with the LDAP search syntax. Some fields contain delimited data that represents multiple object attributes. Your WHERE clause must account for each value in these delimited fields as if they are distinct values, rather than a single string.
For more information about LDAP search filters, see MSDN Search Filter Syntax.
Filtering User on ObjectCategory and ObjectClass
Scenario
You are working with the User table and you want to import records where the ObjectClass has the following attributes:
- person
- user
You also want to limit the records to those where the ObjectCategory has the Computer attribute, and not Person.
Connecting to the table
First, you connect to the Active Directory server, and select the User table (subset of fields shown).
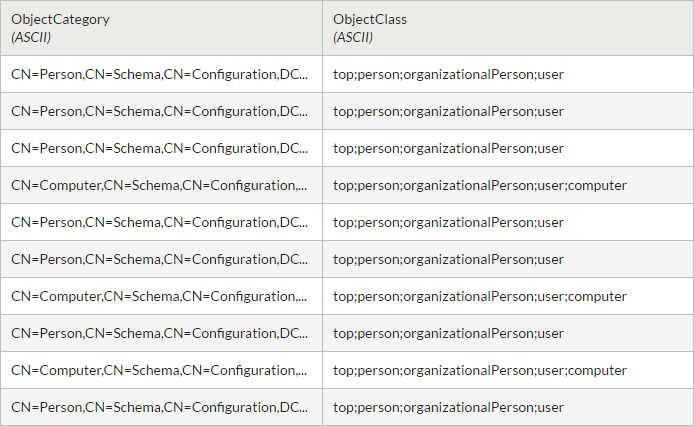
Filtering the records
To limit the records to those you want to import, you apply a filter that treats each delimited value as a discrete field.
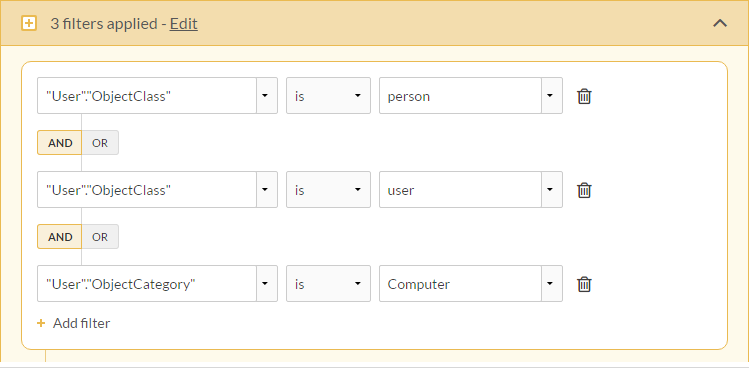
You then use SQL Mode to verify the WHERE clause that the filter constructs:
WHERE
(
"User"."ObjectClass" = N'person' AND
"User"."ObjectClass" = N'user' AND
"User"."ObjectCategory" = N'Computer'
)
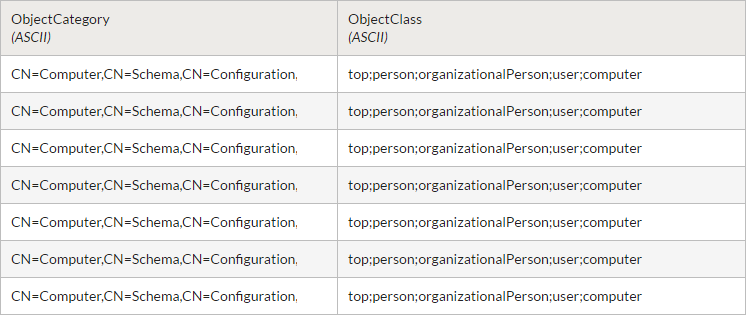
Filter results
Once the filter is applied, the table includes records that match the WHERE clause and you import the table.
Joining Active Directory tables
Due to the data model used in LDAP-compliant databases such as Active Directory, SQL joins are not recommended. Joins may yield unexpected results.
If you need to join one or more tables from an Active Directory data source, you can import multiple tables using the Data Access window and then join them in Analytics. Use filters to limit the number of records and increase efficiency.