Relationships between controls and requirements
Demonstrate your organization's compliance with business-relevant specifications by linking controls to requirements.
Linking controls
A requirement can be covered by many controls, and a control may cover many requirements. When you link a control to a requirement, you define the measures or courses of action for assuring the achievement of an organization's compliance with requirements.
You can only link controls to requirements you have specified as Applicable. For more information, see Creating a compliance map.
Limitations
The maximum number of controls you can link to a single requirement is 300.
What happens when you link a control to a requirement?
On linking controls to a requirement:
- Testing results and issues information are aggregated in a summary view within the Requirement details side panel for each requirement
- Additional controls cannot be linked to the ancestors or descendants of the requirement.
Example
Scenario
You map Requirement 1.2 to Control A.
Requirement 1 - (Control A)
- Requirement 1.1
- Requirement 1.2 - Control A
- Requirement 1.3
Result
-
Control A becomes a related control for Requirement 1.
- You are not able to map additional controls to Requirement 1.
- In order to map Requirement 1 to a different control, you need to remove the existing mapping between Requirement 1.2 and Control A, or map additional controls to Requirement 1.2.
Unlinking controls
At any time, you can unlink controls from requirements. When you do this, the link between the control and requirement is removed, and aggregate testing results and issues information are removed from the compliance map.
When are controls automatically unmapped from a requirement?
If a scenario occurs where controls are automatically unlinked from a requirement, you are prompted to confirm your action in Compliance Maps before the controls are unlinked.
| Scenario | Occurrence | Result |
|---|---|---|
| Specifying a requirement as not applicable | You previously specified a requirement as applicable, linked controls to the requirement, and later decided to specify the requirement as not applicable. |
All controls linked to the requirement and any descendant requirements in its group are unlinked. |
| Changing scope | You change the scope of a standard or regulation and have previously linked controls to requirements that will be out of scope. | All controls linked to out-of-scope requirements are unlinked. |
Related controls
Related controls for a requirement are controls that have been linked to a requirement's ancestors or descendants.
Relationships between controls and requirements are displayed in the Related controls section in the Requirement details side panel for each requirement.
Examples
Example 1: Related controls (Ancestor)
You define the following relationships:
Requirement 1
- Requirement 1.1 → Control A
- Requirement 1.2 → Control B
- Requirement 1.3
Result Relationships between controls and requirements are defined up-tree. The letters in brackets indicate the related controls.
Requirement 1 → (Control A; Control B)
- Requirement 1.1 → Control A
- Requirement 1.2 → Control B
- Requirement 1.3
Example 2: Related controls (Descendants)
You define the following relationships:
Requirement 1 → Control A; Control B
- Requirement 1.1
- Requirement 1.2
- Requirement 1.3
Result Relationships between controls and requirements are defined down-tree. The letters in brackets indicate the related controls.
Requirement 1 → Control A; Control B
- Requirement 1.1 → (Control A; Control B)
- Requirement 1.2 → (Control A; Control B)
- Requirement 1.3 → (Control A; Control B)
Related requirements
Organizations typically need to be compliant with multiple standards and regulations that may have related or overlapping requirements. Related requirements indicate that controls implemented for one requirement should effectively address another (related) requirement.
How it works
Diligent has collated certain related requirements to support efficiency in the linking process. These related requirements may be from the same standard or regulation or from different standards or regulations.
If you have imported standards or regulations from the Compliance Library, you can view related requirements and copy rationale statements from related requirements. For details on the Compliance Library, see Importing standards and regulations, section Manage Diligent-provided standards or regulations .
Note
Use of the related requirements feature is at your discretion and risk, and is subject to the terms and conditions of your subscription. You are responsible to apply professional judgment to determine the appropriate procedures, tests, or controls for your own use.
If the related standard or regulation is not already part of your subscription, or you would like access to other such standards or regulations, please contact your Diligent account representative to acquire access to your desired third-party content.
For more information, see Content & Intelligence Gallery.
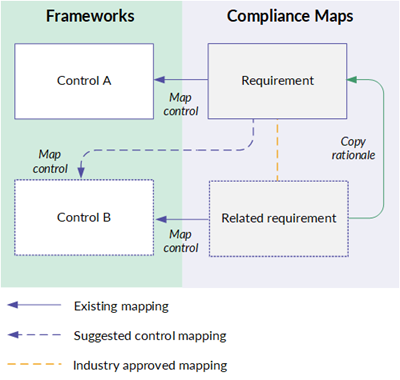
Relationship strengths
Diligent categorizes related requirements using the following relationship strengths:
| Relationship strength | Description | Example |
|---|---|---|
| Equivalent |
Effectively identical Where covering A always requires covering B and vice versa |
|
| Strongly related |
Corresponding or very similar Where covering A usually requires covering B |
|
| Moderately related |
Some overlapping elements Where covering A sometimes requires covering B |
|
Suggested controls
If you previously linked a control to a related requirement, the control mapping is displayed as a suggestion in Compliance Maps. These suggestions help compliance teams show adherence to multiple standards and regulations more efficiently and expedite the control mapping process.
You can choose to map suggested controls to a requirement or dismiss the suggestion. Dismissing a suggestion permanently removes it for all users in the Diligent One instance. Once dismissed, the suggestion is never presented for the requirement again.