Configuring Single Sign-On (SSO)
SSO is an authentication process that allows users to access multiple applications after only signing in once. Diligent One supports SSO integration for any identity provider that adheres to the OASIS SAML 2.0 protocol.
You can set up more than one SSO provider for an organization.
About Single Sign-On
-
Multi SSO configuration Customers can configure more than one Single sign-on provider within one organization.
-
Switching between SSO and non-SSO organizations If you are switching between an SSO-enabled and a non-SSO organization, you will be prompted to enter your Diligent One credentials. If you don’t have this credential, then you must set up a password by selecting the Forgot password? link. If you would like to authenticate using SSO for all your orgs, inform your system administrators to configure SSO for the non-SSO organizations. For more information, see Configuring Single Sign-On (SSO).
-
System administrator's sign-in experience for SSO orgs System administrators can now sign in to SSO organizations using their Diligent One Platform email and password. This is to allow our customers to reconfigure their SSO configurations via their System Admins in the case where users cannot authenticate into their organization. System Admin can also select certain users within the org to bypass SSO.
-
Diligent One Platform does not support just-in-time (JIT) provisioning To align with best security standards, we do not support just-in-time provisioning. Coordinate with your system administrator to enable external user provisioning (for example, SCIM) if you would like to automate your organization’s user provisioning process.
-
Use public certificates instead of security fingerprint While configuring a new SSO provider or updating a current one, you must enter the public certificate instead of security fingerprint.
When you configure or update SSO, enter the public certificate (including the BEGIN CERTIFICATE and END CERTIFICATE lines), which has the following format:
-----BEGIN CERTIFICATE-----
<certificate content here>
-----END CERTIFICATE-----
Permissions
Only System Admins can configure SSO settings for their company.
Requirements
- Your identity provider must adhere to the OASIS SAML 2.0 protocol.
- All users of an SSO-enabled instance of Diligent One must authenticate through an identity provider.
If your users access multiple organizations
Users who authenticate through an identity provider can do so for multiple Diligent One organizations if all of these organizations belong to the same company.
To check this, look at "Customer name" in the organization settings for each organization. It must be the same in all organizations that SSO users need to access. For more information, see Updating organization settings. Alternatively, you can use the instance switcher to verify that the organizations in question are indented below the same company name. For more information, see Switching between Diligent One organizations.
If you need to change which company your instance belongs to, contact Support.
Authentication is not region-specific. Users can access Diligent One instances in multiple regions.
If your users access training organizations
Users who authenticate through an identity provider can create training organizations, which are automatically linked to the same company.
Additional users can be added to these organizations as long as they do not already belong to a different training organization with the same email. These users must set up a password to access the Diligent One training organizations by selecting the Forgot password? link on the sign in page.
If your users work for multiple companies
Users working for multiple companies can use SSO. When logging in, they are prompted to authenticate with the SSO configured for the specific company they are accessing.
If you want to use SSO and 2FA together
You can exempt users from SSO authentication, allowing them to log in using the standard process with 2FA. For more information, see Adding users to allow list to bypass SSO.
Setting up SSO identity providers
-
Open the Platform home page (www.diligentoneplatform.com).
Note
Diligent One Platform also supports the domain www.highbond.com. For more information, see Supported domains.
- From the left navigation, select Platform Settings.
The left navigation displays the different platform settings options. - Under Organization management, select Security settings.
- On the Security settings page, in the Single sign-on (SSO) options section, select Set up provider.
- On the Single sign-on set up panel, enter the details as described in the following table:
Field Description Custom domain The unique name that identifies your instance, and enables users in your company to sign in to Diligent One. The custom domain is your instance's subdomain appended with a region code.
NoteYou can change your instance's subdomain on the Update Organization page. For more information, see Updating organization settings.
Name Enter a name for the identity provider. Entity ID The URL that identifies the identity provider issuing a SAML request. This is a URL specific to your identity provider. Metadata URL The URL that Platform home can access to obtain SSO configuration data from your identity provider. This is a URL specific to your identity provider. Redirect login URL The URL of your identity provider for users in the company to sign in to Diligent One. Logout URL The URL to which Diligent One will redirect the users in the company after they sign out of Diligent One. Public certificate The certificate that is issued to verify the device and the user. - Select Enable.
The Single sign-on (SSO) options section displays the identity provider that you added.
Adding users to allow list to bypass SSO
When you add multiple authentication options, you can exempt users from using SSO authentication. Typically, this exemption applies to users who are not members of any identity providers. These exempted users can continue to sign in with their username and password.
-
All System Admins automatically receive SSO bypass permissions.
-
If two-factor authentication (2FA) is enabled for your organization, it applies to all users, including those with permission to bypass Single Sign-On (SSO). Therefore, it’s important to review user access to ensure no one is unintentionally locked out of the platform.
- On the Single sign-on (SSO) options section of Security settings, select the +Add users tab next to the Users with permission to bypass SSO section.
- In the Users with permission to bypass SSO panel that appears, select the users whom you want to exempt from using the SSO authentication.
- Select Add users.
You can use the Search field to find users.
The users added to the list to bypass SSO appear in the Users with permission to bypass SSO section.
Removing users from allow list to bypass SSO
To remove users added to the allow list to bypass SSO, in the Users with permission to bypass SSO section, select the remove icon that appears next to the user that you want to remove.
System Admins can't be removed from the allow list. All System Admins automatically receive bypass permissions.
Disabling SSO identity providers
- On the Security settings page, in the Single sign-on (SSO) options section, select Open details for the identity provider you want to disable.
- In the Single sign-on set up panel, from the dropdown menu of the Status field, select Disabled.
- Select Save changes.
- In the Confirm disabling SSO provider dialog box that appears, select Confirm.
The SSO identity provider is marked as Disabled in the Single sign-on (SSO) options section.
After disabling an SSO provider, users in your organization can no longer sign in with the provider. However, the provider's information remains saved.
Enabling a disabled SSO identity provider
- On the Security settings page, in the Single sign-on (SSO) options section, select Open details for the identity provider you want to enable.
- In the Single sign-on set up panel, from the dropdown menu of the Status field, select Enabled.
- Select Save changes.
The SSO identity provider is marked as Enabled in the Single sign-on (SSO) options section.
Removing SSO identity providers
- On the Security settings page, in the Single sign-on (SSO) options section, select Open details for the identity provider you want to remove.
- In the Single sign-on set up panel, select Remove.
- In the Confirm removing SSO provider dialog box that appears, select Confirm.
After you remove an SSO provider, users in your organization can no longer sign in with this SSO provider. The provider's information also gets deleted.
Diligent One Platform service provider URLs
When configuring your SSO identity provider, you require the following service provider URLs for Diligent One Platform:
- One of the service provider entity ID
- https://accounts.diligentoneplatform.com/saml/metadata/your_custom_domain
- https://accounts.highbond.com/saml/metadata/your_custom_domain
Tip
The entity ID URL also serves as the metadata endpoint for Diligent One Platform.
- One of the service provider assertion consumer URL
- https://accounts.diligentoneplatform.com/saml/sso/consume/your_custom_domain
- https://accounts.highbond.com/saml/sso/consume/your_custom_domain
Note
Support for www.highbond.com ends on July 31, 2026.
Using the Service Provider metadata file
After SSO is enabled for your organization, you can access the service provider metadata file, which can be uploaded to your identity provider.
-
Copy one of the service provider entity ID URLs:
- https://accounts.diligentoneplatform.com/saml/metadata/your_custom_domain
- https://accounts.highbond.com/saml/metadata/your_custom_domain
-
Paste the URL into a web browser.
The metadata XML file is downloaded to your system.
-
Upload it to your identity provider.
Logging in when SSO is enabled
There are two ways users can log in when SSO is enabled.
What happens when SSO is enabled?
When SSO is enabled, you can sign in by going to www.diligentoneplatform.com, clicking Continue with SSO, and providing your custom domain.
Note
Diligent One Platform also supports the domain www.highbond.com. For more information, see Supported domains.
Alternatively, you can access Diligent One using the Diligent One app link from your identity provider landing page.
You are redirected to Diligent One via your identity provider when you access any Diligent One apps (including clicking on a link in an email sent from Diligent One).
-
When SSO is enabled, you can't sign in with your email and password or change your password. However, if you are a System Admin or a user who is listed as one who can bypass SSO, you can sign in with your email and password.
-
You can't change email addresses if SSO is enabled in your organization. However, if your organization has enabled both SSO and SCIM, email addresses can be changed.
-
For an organization where only SSO is enabled, updated email addresses are treated as new accounts, preventing users from accessing information associated with their previous credentials. Therefore, for such organizations, if email addresses need to be changed, the System Admin must first disable SSO in Diligent One, update the email addresses, and then re-enable SSO.
-
For an organization where SCIM is enabled, email address changes from your identity provider are automatically reflected in Diligent One Platform.
Do I need to enter my custom domain each time I sign in?
- If you sign in through your identity provider, you do not have to provide a custom domain each time.
- If you sign in through Diligent One, you can access one of the following URLs to avoid entering a custom domain each time:
- https://accounts.diligentoneplatform.com/saml/sso?custom_domain=your-custom-domain
- https://accounts.highbond.com/saml/sso?custom_domain=your-custom-domain
Note
Support for www.highbond.com ends on July 31, 2026.
Signing into multiple organizations of Diligent One
If you have access to multiple organizations of Diligent One, you are brought to the organization you used most recently. If you belong to both SSO-enabled and non-SSO organizations, you must set up a password to log in to the non-SSO organization. To do so, select the Forgot password? link.
If you have access to multiple organization of Diligent One, you can easily switch between them. For more information, see Switching between Diligent One organizations.
When switching between organizations, you will be prompted for the authentication credentials of the organization you are switching into if you have not already authenticated with that organization.
Logging out when SSO is enabled
Diligent One supports SLO (Single Logout) using the identity provider initiated workflow.
Use one of the following SLO URLs:
-
https://accounts.diligentoneplatform.com/saml/slo/your-custom-domain
-
https://accounts.highbond.com/saml/slo/your-custom-domain
Note
Support for www.highbond.com ends on July 31, 2026.
How session expiry works
When a Diligent One session expires, or when you attempt to log out of Diligent One, you must first log out of your identity provider. Otherwise, you are automatically signed back in to Diligent One.
For example, if your organization's session expiry is three hours and your identity provider's session expiry is three days, you will be automatically signed in to Diligent One for three days.
For security purposes, your company should ensure that your identity provider's expiry is less than your instance's session expiry.
You can change your organization's session expiry on the Update Organization page. For more information, see Updating organization settings.
Adding users to an SSO-enabled Diligent One organization
Diligent One supports SCIM external provisioning. If your identity provider has SCIM as an option, you can provision users into the platform automatically. However, if your identity provider does not have SCIM, you must add your SSO users manually into the Diligent One organization for them to access the platform.
Subscriptions and access to Diligent One apps
The user will have no subscriptions assigned, nor access to any Diligent One apps. System Admins must assign users a role and subscription in Platform home to ensure users have appropriate access in the instance.
Disabling SSO
If your company enables SSO, and later decides to disable it:
- Users who did not set up a password before SSO was enabled must select Reset password on the sign in page to obtain a password.
- Users who set up a password before SSO was enabled can sign in with their user name and password.
SSO and SAML
Diligent One supports SSO integration for any identity provider that adheres to the OASIS Security Assertion Markup Language 2.0 (SAML 2.0) protocol. OASIS SAML 2.0 is a format for communicating and authenticating identities between two web applications.
OASIS SAML 2.0 involves:
- A user requesting service.
- A service provider or application providing service (Diligent One).
- An identity provider or repository that manages user information.
For instances with SSO enabled, users are authenticated when they sign in to Diligent One using a supported SAML identity provider. If the user is not enabled in their company's SAML identity provider, the user is denied access.
Supported workflows
After SSO settings are configured, the following workflows are supported:
- Identity provider initiated - Accessing Diligent One from the identity provider landing page.
- Service provider initiated - Accessing Diligent One from the Diligent One home page.
Configuring SAML 2.0 integration with Okta for Diligent One Platform
Configuring SAML 2.0 with Okta involves steps in Diligent One Platform and Okta.
Steps to be performed in Diligent One Platform
- From the left navigation, select Platform Settings.
The left navigation displays the different platform settings options. - Under Organization management, select Security settings.
- On the Security settings page, in the Single sign-on (SSO) options section, select Set up provider.
- On the Single sign-on set up panel, copy and paste the corresponding values from your Okta Administration Sign On tab. The fields are described in the following table:
Field Okta Administration SAML 2.0 value Custom domain Not applicable in Okta.
This field is for the unique name that identifies your instance, and enables users in your company to sign in to Diligent One. The custom domain is your instance's subdomain appended with a region code.
NoteYou can change your instance's subdomain on the Update Organization page. For more information, see Updating organization settings.
Name Not applicable in Okta.
Enter a name for the identity provider.
Entity ID Issuer
Metadata URL Metadata URL
The URL that Diligent One Platform can access to obtain SSO configuration data from your identity provider. This is a URL specific to your identity provider.
Redirect login URL Sign on URL
Logout URL Sign out URL
Public certificate Select Download next to Signing Certificate.
Open the certificate with a text editor.
Copy and paste all the values into the Diligent One Platform Public certificate field.
- Select Enable.
Steps to be performed in Okta
-
Navigate to Applications > Applications > Browse App Catalogue, and search for Diligent One.
-
Select the General tab for the Diligent One SAML app, the select Edit.
-
In the Custom Domain field, enter the value that you have from the Diligent One SSO setup.
-
Select Save.
You can now authenticate through the Diligent One tile in your Okta dashboard.
To log in through the SP-initiated (service provider initiated) SSO, follow these steps:
-
Select Continue with SSO.
-
On the Sign in page, enter your custom domain and select Continue.
If you are not already signed in, you are prompted to log in through Okta.
Identity provider initiated authentication process
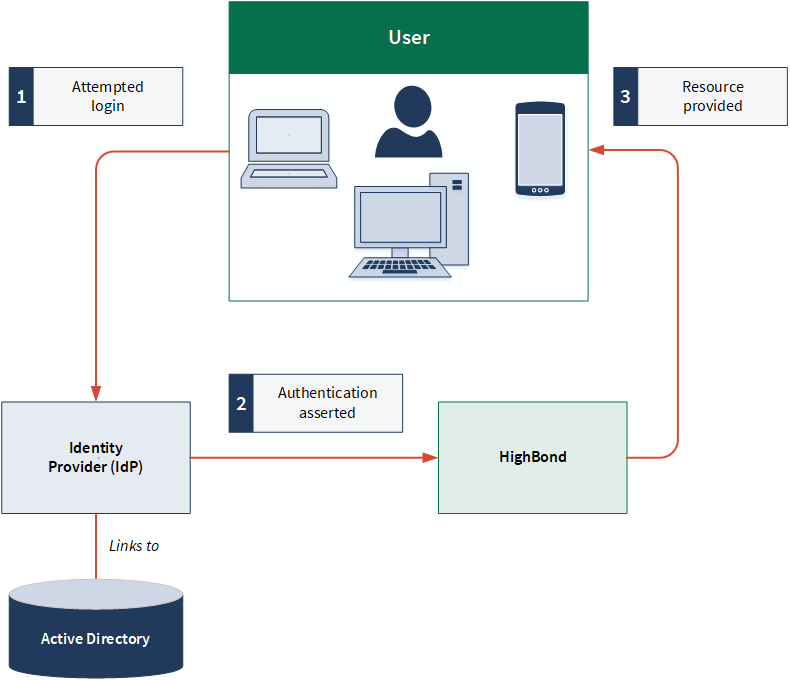
Service provider initiated authentication process
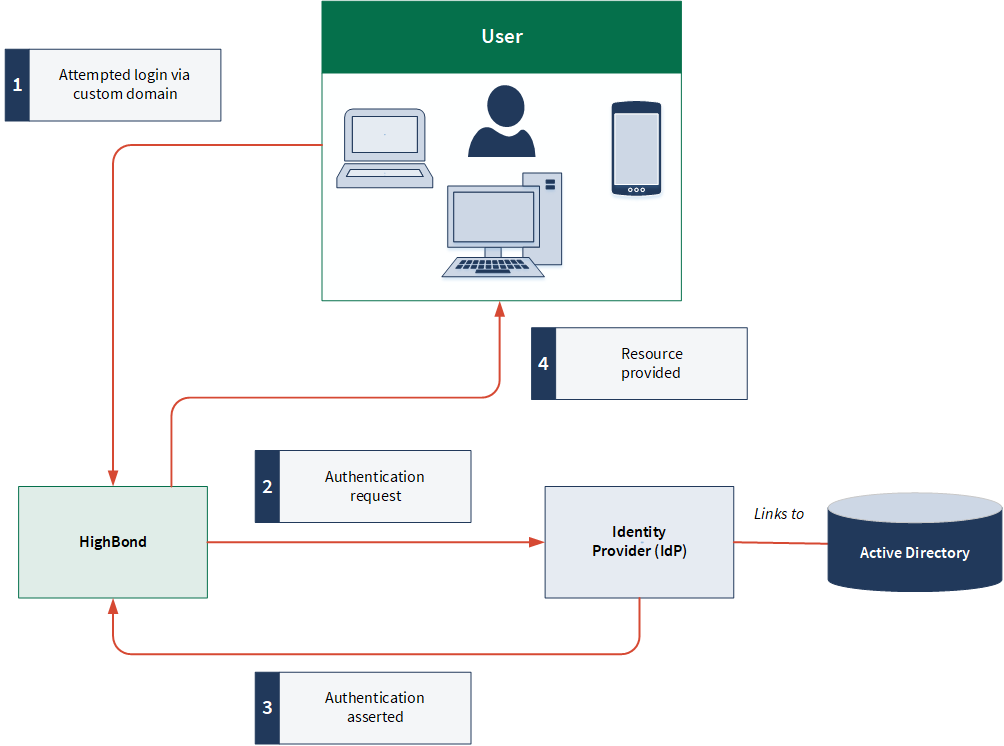
Offboarding users who leave
When users leave your company, your offboarding process removes them from your identity provider. The impact on users varies depending on the organizations they were associated with and the specific configurations of those organizations.
- If users were part of only your SSO-enabled organizations, they can no longer access those organizations on Diligent One.
- If users belonged to both your SSO-enabled organizations and other non-SSO organizations:
- If you remove the user from your identity provider, you must ensure that the users are removed from Diligent One organization. The System Admin must offboard the users from other non-SSO organizations.
- If you manually remove users from the SSO-enabled organizations, they can still access non-SSO instances after they reset their password.