Managing third-party assets
A TPRM environment usually comprises multiple third-parties. You can use the third-party asset inventory to onboard and manage the life cycles of your third-parties, launch assessments, and calculate criticality levels and risk scores. Further, you can use the risk scores and findings to prioritize tasks and identify and remediate potential risks.
A combination of various elements helps set up a robust TPRM framework. Third-party Asset Inventory is a key piece of this framework and works with many underlying elements.
Elements in a TPRM Asset Inventory
Supporting elements in a third-party asset inventory primarily include the third-parties involved, users, workflow states of the life cycle, and assessments. All these elements are presented as different attributes in the asset inventory to collect information against a third-party. When you collect and update all this required information in Third Party Risk Management, you can start monitoring and assessing different third-parties and eliminate risks promptly.
| TPRM Element | Description | Example |
|---|---|---|
|
|
Represents a third-party being assessed. | Products, vendors, partners, and service providers |
|
|
Roles are assigned to users to own, initiate, progress, monitor, and complete the third-party life cycle. | Risk Manager, Business Owner, Third-party Owner |
|
|
Different stages of a third-party life cycle during which users enrich attributes, trigger assessments, calculate risk ratings, and review the results. |
Draft, Registered, Categorized, Active, Archived |
|
|
Questionnaires that are sent out to users to collect responses, which help calculate the criticality levels or risk scores. |
Categorization assessment (SIG Lite or CAIQ Lite) |
How it works
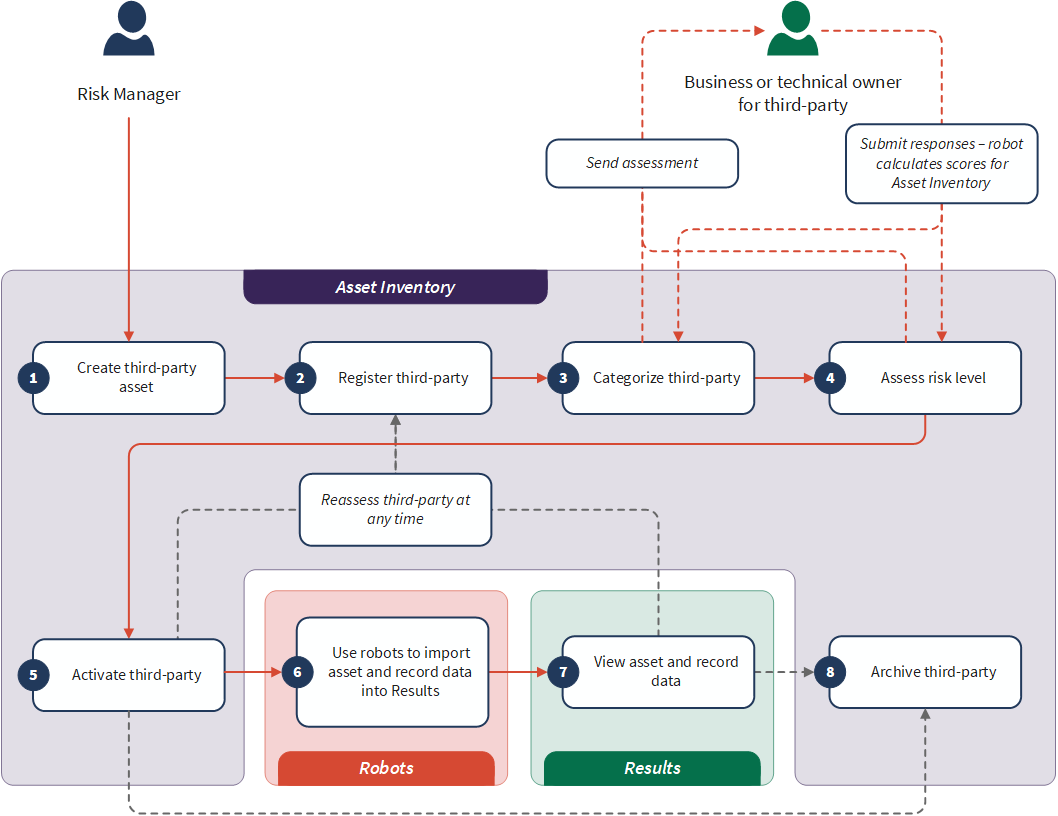
The Third Party Risk Management workflow mainly takes place in the Asset Inventory app:
- Create third-party asset Add a third-party asset to Asset Inventory.
- Register third-party Add critical details to your asset, so it's ready for the risk assessment process.
- Categorize third-party Use an automated criticality assessment to prioritize your third-parties, identifying the ones that are mission-critical to your organization.
- Assess risk level Use an automated standard risk assessment (SIG Lite or CAIQ Lite) to assess third-party risks and create findings to address.
- Activate third-party Approve and activate your third-party, so you can start mitigating risks associated with it.
- Use robots to import asset and record data into Results Use a Workflow robot to import asset and record data into Results. In Robots, you can also manage import settings; for example, you can set the Workflow robot to import data at the same time every day.
- View asset and record data View the imported data in Results, in dedicated tables, so you can monitor your risk mitigation efforts and identify remaining action items.
- Archive third-party If required, you can archive a third-party so you'll still have a record of the information associated with it, but you'll know you don't have to mitigate risks for it anymore.
1. Create a third-party asset
A third-party is identified and managed as an asset in Third Party Risk Management. For each third-party you assess, you must enter it as an asset into Asset Inventory.
When you add a third-party, it enters the
Scenario
Your organization partners with 5 third-parties, and as a Risk Manager, you are assigned to add all the third-parties in Third Party Risk Management to begin their life cycle management.
Steps to add third-parties
First, create all 5 third-parties as assets in Third Party Risk Management, one for each third-party being assessed. For each third-party you add:
- In Asset Inventory, click the Third-party asset type, then click Add Third-party.
- In the Add Third-party dialog box, enter a name for the third-party and click Add.
For detailed steps, see Working with assets.
Result
After adding a third-party asset, the asset details page appears and you can proceed with the rest of the workflow. When you navigate back to the Third-party Asset Inventory dashboard, you can see all of your organization's third-parties and view details about them.
Registration and categorization help you prioritize third-party tasks and remediate risks associated with them.
2. Register the third-party
When registering a third-party asset, you need to add more critical details to advance it to the next workflow state in the asset life cycle. You can view and edit an asset's attributes on the Details tab. The following attributes are mandatory to register a third-party asset:
- Business Owner User responsible for all information corresponding to a third-party asset. For example, a primary business contact for a third-party asset, from a particular department or procurement team.
- Risk Manager User responsible for progressing the third-party life cycle by analyzing the assessment responses and records. For example, a TPRM Analyst in your organization.
- Third-party Type Specifies whether the asset is a third-party product or service. For example, a subscription to a cloud-based service can be a Service, whereas an on-premise user access control system can be a Product.
- Third-party Description A brief description of the third-party asset.
To register a third-party asset:
- Enter values for the above mandatory attributes and any other attributes as applicable and click Save changes.
-
In the visual workflow available at the top of the page, select
Draft > Register orActions > Register .Result Third Party Risk Management validates that the third-party asset has all mandatory values and moves it to the Registered state.
3. Categorize the third-party
Categorizing a third-party involves assessing the criticality impact a third-party has to an organization and assigning a criticality level to it. Assigning the correct criticality level to a third-party is important as it defines the amount of scrutiny and diligence that must go into activities related with the maintenance of this asset.
What is a criticality level?
Criticality level indicates the level of impact the risks associated with a third-party may have on your business. Various factors play a role in determining the criticality level of a third-party, such as access to sensitive information including customer details, disruption of business, financial importance, and reputation.
The criticality levels available in Third Party Risk Management are:
- Critical
- High
- Medium
- Low
The following table shows an example of the criticality levels assigned to different third-parties partnering with an e-commerce firm.
| Third-party | Criticality aspect on business | Criticality level |
|---|---|---|
| Payment gateway service | Outage would definitely disrupt business | Critical |
| Transaction billing service | Outage may disrupt business | High |
| CRM service | Outage would not disrupt business, but could lower customer satisfaction | Medium |
| Office stationery | Outage would not disrupt business and poses no other immediate risk | Low |
The mandatory attribute to categorize a third-party asset is Third-party Criticality Level.
You can either use your organization's internal assessment metrics and assign the criticality level for a third-party or use the categorization assessment provided with the solution.
Determining criticality levels through categorization assessments
For more information on determining criticality levels through categorization assessments, see Assessment scoring for third-party assets.
You can initiate the categorization process either by selecting Registered > Categorize in the visual workflow or
Scenario
You have registered 5 third-party assets and now want to categorize them. Using internal metrics and calculations, you assign the criticality levels for 4 third-parties. You notice that the criticality level of one third-party has not been assessed due to missing information. You decide to use the categorization assessment provided in the solution.
Steps to categorize third-party assets
For each of the 4 third-party assets you entered the criticality levels for, open the corresponding asset detail page. On the Details tab, select the appropriate level in the Criticality Level field. Save the details and select Pending Categorization > Approve.
For the third-party for which you want to determine the criticality level, open the asset detail page and select Pending Categorization > Launch Categorization Assessment. In the Send questionnaire panel, enter the name or email address of the person (usually the third-party asset's Business Owner) who can enter the required information. When they submit their responses, Diligent One calculates the criticality level and automatically assigns it to the third-party asset. Verify the score and select Pending Categorization > Approve.
Result
The third-party assets are now categorized based on criticality levels and moved to the
Skip risk assessment for a low criticality asset
There may be scenarios where you have low criticality third-parties (for example, a vendor that supplies office stationery) and do not want to spend time assessing risks associated with those assets. In such a case, after categorizing the third-party asset, you can skip the risk assessment steps.
To skip the risk assessment process:
-
Select Categorized > Review from the visual workflow or Actions > Review.
The third-party asset moves to the Pending Review state.
- On the Details tab, provide values in the Overall Risk Rating and Rationale for Rating fields and click Save changes.
-
Select Pending Review > Activate.
The third-party asset moves to the Active state.
Once activated, if you want to assess the risk of the third-party at any point of time, you can use the (Optional) Reassess the third-party workflow.
4. Assess risk level
Risk assessments are critical to identify risks associated with third-parties. You can generate the risk assessment for a third-party and distribute it to an identified respondent, typically a Third-party Owner. Once the respondent submits their responses, Diligent One calculates the risk score and level and automatically populates them in the SIG/CAIQ Lite Risk Level and Risk Score fields. You can use these risk scores to identify risks, create remediation plans, and continue or terminate the services of the third-party.
Generate a risk assessment
Third Party Risk Management supports two assessment models: SIG Lite and CAIQ Lite. You can generate one of these assessments, based on the version of the Third Party Risk Management toolkit that your organization subscribes to.
To generate a risk assessment, select Categorized > Risk Assess in the visual workflow or Actions > Risk Assess. Third Party Risk Management generates the risk assessment and the third-party moves to the Pending Assessment state.
You can further distribute this assessment to a corresponding Third-party Owner.
Collect responses for your risk assessment
After generating a risk assessment, you must distribute it to its Third-party Owner to collect responses.
To send the risk assessment to the Third-party Owner, select Pending Assessment > Launch Risk Assessment in the visual workflow or Actions > Launch Risk Assessment. In the Send questionnaire panel, select the questionnaire to send, and enter the name or email address of the person (usually the third-party asset's Third-party Owner) who can enter the required information, and click Send.
Review and accept risk level
Diligent One automatically generates a risk score and level for a third-party asset based on the assessment responses. Risk score is a percentage value and risk levels can be Critical, High, Medium, or Low. For more information on how Third Party Risk Management calculates risk scores, see Assessment scoring for third-party assets.
A Business Owner can review the risk level and score and select Pending Assessment > Accept Risk Level or Actions > Accept Risk Level. Diligent One validates the that the third-party has a risk score and level assigned and moves it to the Pending Review state.
Scenario
A third-party asset in your environment has a high criticality level and you must assess the risk level to determine if you need to create any remediation plans.
Steps to assess risk of a third-party asset
- The Risk Manager opens the third-party asset details page and selects Categorized > Risk Assess.
-
They send the generated risk assessment to the Third-party Owner.
- The Business Owner reviews the risk levels and selects Pending Assessment > Accept Risk Level.
Once the Third-party Owner submits their responses, Diligent One calculates the risk score and level and populates it in the Risk Level and Risk Score fields.
Result
The third-party asset is now risk assessed and moves to the
Track issues with findings
If you find an issue with a third-party asset that you need to address, you can do so by creating a finding.
When viewing an asset, on the Overview tab, you can expand the Findings drawer to view all the findings associated with that asset. Here, you can create findings, or track the work required to address existing findings.
Scenario
While completing the CAIQ Lite questionnaire, the Third-party Owner realizes that you don't test your backup or recovery mechanisms on an annual basis. They notify you that this is something that you should look into together, so you create a finding to track that work.
Steps to address a finding
- To create a new finding, you click Add Finding, enter a name for the finding, and click Add. Third Party Risk Management saves your finding and automatically assigns it the Open status. You fill in the relevant attributes for the finding and click Save changes.
- When you're ready to work on the finding, in the visual workflow, you click Open > Start. The status changes to In Progress. You begin to create a plan to schedule annual tests, and list what those tests will consist of.
- When you're ready to submit your plan for review, click In Progress > Review. The status changes to Pending Review. You ask the Third-party Owner to review your plans.
- After the review is complete, click Pending Review > Close. The status changes to Closed.
Result
You have addressed the issue raised while the Third-party Owner completed the questionnaire, and are confident that your third-party will be more secure as a result.
5. Activate the third-party
Now that a Business Owner has reviewed and approved the risk score and level, as a Risk Manager, you can review the attributes on the Details tab and activate the third-party. The mandatory attributes to activate a third-party are:
- Overall Risk Rating - Select an overall risk rating depending on the criticality and risk level of the third-party. You can select a value from Critical, High, Medium, and Low.
- Rationale for Rating - Provide your reasoning for specifying the rating.
To activate the third-party, save the details and select Pending Review > Activate or Actions > Activate. If values are provided for the required attributes, the third-party moves to the Active state.
6. Use robots to import asset and record data into Results
After activating your third-parties and beginning to mitigate associated risks in Asset Inventory, you can use Workflow robots to import asset and record data into Results, so you can see it all in one place.
Permissions and installation
Like all other Workflow robots, you must be assigned the System Admin user type with a Professional subscription to work with these robots.
From the dashboard in Robots, select Workflow Robots and look for the Assets Reporting and Records Reporting robots. Older installations of Third Party Risk Management didn't include these robots, so if you don't see them, contact your Diligent representative for assistance.
Using the robots
For each robot, you can decide to run it as needed, or you can schedule it to run regularly (e.g., once per day). For more information, see Creating a robot task to run a script.
Every time you run one of these robots, it recreates the data in Results from scratch, so you don't have to worry about seeing duplicates from existing third-parties, or out-of-date data from third-parties that you've deleted.
The scripts in these robots include some elements that can be customized. For example, you can customize the labels for some fields so that they appear differently in Results. You can contact your Diligent representative for assistance making these customizations. If you are comfortable editing the scripts, you can make the customizations yourself. For more information about scripting in Robots, see Python and HCL scripting in Robots .
7. View asset and record data
In Results, data imported using Workflow robots is saved in the Risk Management Reporting collection. If you navigate to that collection, you can find the results tables that match the names of the robots you used and view the most recently imported data. For more information, see Overview of Results.
(Optional) Reassess the third-party
Third-parties that are critical from business and security standpoints often need to be assessed periodically. You may also want to reassess other third-parties when there are any changes to existing terms and policies. When you select Active > Re-assess, Diligent One moves the third-party back to the Registered state. You can restart the categorization and risk assessment processes.
8. (Optional) Archive the third-party
If you no longer need to monitor a third-party but still need to keep a record of it in the system, you can archive the asset. Select Active > Archive.
For ease of use, Third Party Risk Management allows you to archive a third-party asset from any stage after adding it.
Note
Once you archive a third-party asset, you cannot revert or make any further updates in the life cycle. However, if needed, you can always create a new asset.
You can also