Implementing a compliance program
Incident reporting and investigations are critical components of a robust compliance program. Without the right resources to identify and respond to incidents, and investigate allegations of wrongdoing, an organization can suffer serious financial damages — and its credibility with regulators can also be called into question. In this article, we discuss how to implement and automate a compliance program using the Results and Storyboards apps.
This article builds on the examples illustrated in Demonstrating compliance, and provides an approach that would enable an organization to comply with the COBIT® 5 Framework. However, the same workflow can also be applied to implement and automate compliance programs involving:
- regulations applying to financial institutions, such as Truth-in Lending, Anti-Money Laundering, or Depository Insurance
- other IT security frameworks, such as ISO or NIST
- Data Privacy regulations, such as the EU GDPR, GLBA, HIPAA, and FERPA
- regulations applying to government or higher-education, such as Uniform Grant Guidance, Single Audit, or Title IV
What's involved?
Implementing and automating a compliance program involves two key processes:
- developing programs to identify and respond to incidents, typically using tiered or escalated response systems
- conducting investigations to monitor and manage the details of one or more incidents
Incident reporting and investigations can be carried out throughout the compliance management process, allowing evaluators to:
- capture incidents via data analytics
- define triggered workflows for managing incidents
- perform root cause analysis and remediation activities
- close cases once they are ready for reporting
Where do I implement and automate a compliance program?
At Diligent, we use the Results and Storyboards apps to implement and automate our compliance program. We have implemented a security policy framework based on ISO 27001/2 to define minimum security requirements and expectations for security across the organization.
Our incident response program, which supports our overall compliance program, involves monitoring and investigating all events and reports of suspicious or unexpected activity. If an incident is confirmed, analysis begins, a severity is assigned and the record is escalated accordingly. Depending on the severity and incident type, our team gathers and analyzes information, involving forensic specialists as required, to determine the causes, impact, type and any other relevant information regarding the incident.
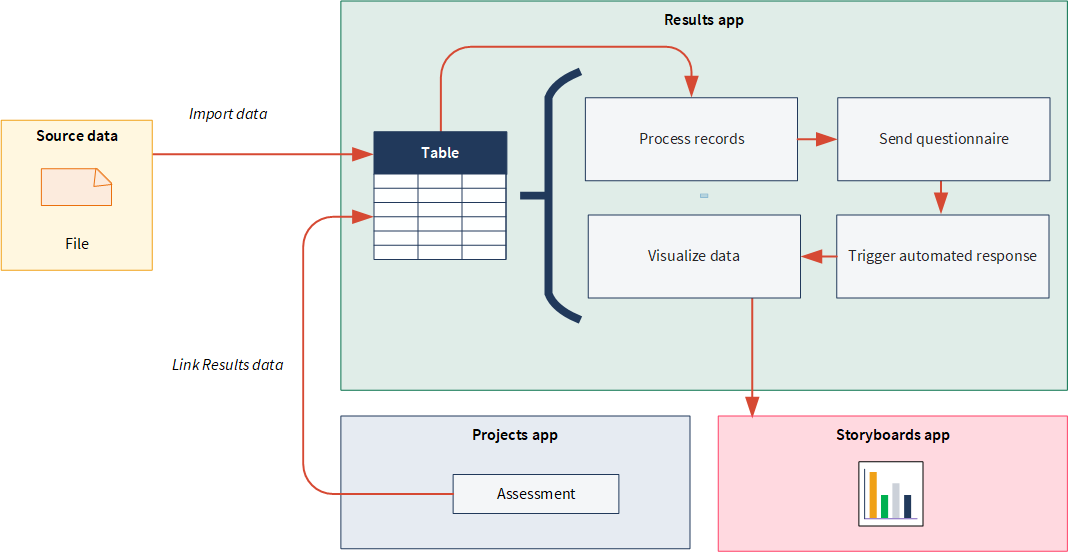
The big picture
- Questionnaires are used to contextualize data and responses are stored in Tables.
- Triggers automate your organization's remediation processes by executing a set of actions based on record data in a Table.
- Storyboards present data results using multiple visualizations, which is based on record data in Tables.
Once you've conducted the required investigations, you can link Results data to your assessments in the Projects app to consolidate information and easily sign-off when remediation is complete.
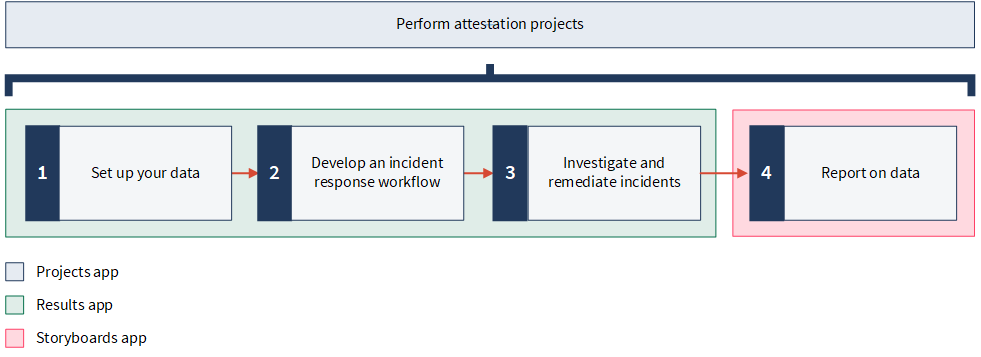
Steps
Ready for a tour?
Let's take a closer look at these features in context.
1. Set up your data
The first step is to set up and organize your data in Results. There are three levels of organization for data: Collections, Analyses, and Tables. Data is stored in tables called Data Analytics. Each table is contained within an Analysis and a Collection.
Example
Scenario
As an IT security professional, you need to perform a review of critical system access events that occurred within the last three months (April - June, 2018). For your organization to comply with the COBIT® 5 Framework, you need to ensure that only authorized employees have access to critical systems.
You want to import your source data into a central location, so that you can begin conducting investigative work.
Process
Help topic Setting up Results
You set up the following data containers in Results:
- Collection Application Systems Operational Processes Monitoring
- Analysis System Access Management
- Data Analytic Privileged User Access
You then import your source data file into the Data Analytic.
Result
The source data is imported and displayed in a table.
2. Develop an incident response workflow
After you have set up your data containers in Results, you can develop an incident response workflow to route incidents for investigation and corrective action. Root cause analysis can be automated by triggering an alert (in the form of email notifications) to key personnel who can drill down to individual incident details to determine the circumstances behind the incident.
Tip
Incident data capture can also be automated using event reports. Organizations can efficiently collect whistleblower data to identify unethical behavior, take corrective action, and forecast future risk mitigation efforts.
Create questionnaires
Questionnaires are used to gather information from respondents and contextualize data. Each collection can have one or more questionnaires that you deploy as follow-up mechanisms when remediating records. Responses are captured in the specified table with each question defined as a distinct column.
Tip
The Template Questionnaires Collection contains a variety of pre-built questionnaires that you copy and use as a starting point. Each template questionnaire relates to different industry segments and is pre-populated with a series of questions.
Example
Scenario
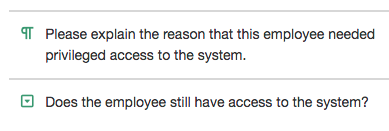
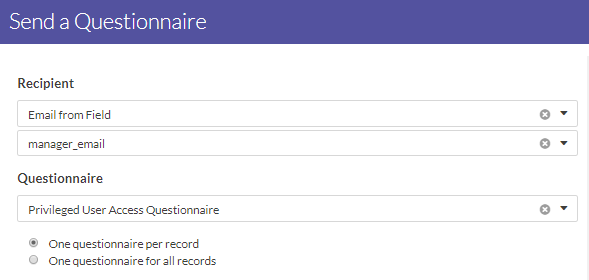
To follow-up on the critical system access records, you want to send a questionnaire to the manager emails you have on file. This way, you can understand the reason for giving the employee privileged access, and whether or not they still have access to the system.
Process
Help topic Creating questionnaires
You create a short questionnaire to gather more information, and link the questionnaire to the Data Analytic.
Result
You can now send the questionnaire to gather additional information from respondents and contextualize data.
Define a triggered workflow for managing incidents
Depending on the severity of the incident captured, triggers can be set up to send out emergency mass notifications to larger teams in a crisis management situation. For isolated incidents, root cause analysis can be performed by using individual workflows coupled with questionnaires to solicit feedback from process owners to determine the root cause of an incident captured.
Tip
Because incident management may involve different departments or teams that take part in investigating exceptions, workflow groups can also be used to build an incident management workflow based on each department's unique policies and procedures. For example, a Finance team may need to assign a transaction representing an expense policy violation to be reviewed by the manager of the affected department, whereby only a Finance team member will be able to "close” the issue once resolved.
Example
Scenario
Your team compares logged critical system access events with a sanctioned user list and employee termination date from Active Directory. Any potential unauthorized access must be escalated to critical priority and assigned to the appropriate team member for investigation and remediation.
For your team to efficiently identify and respond to incidents, you need to create an automated critical incident response workflow.
Process
Help topic Create a trigger
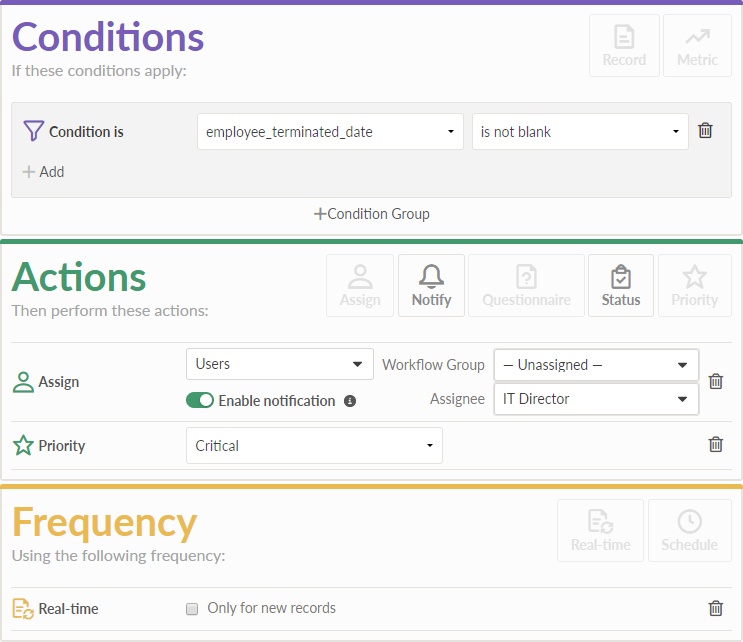
You configure a real-time trigger on records with two conditions:
- employee_terminated_date is not blank
- the response to the question "Does the employee still have access to the system?" contains "Yes"
The trigger takes the following actions when records are updated:
- escalates the priority of the record to critical
- assigns the record to the IT Director for investigation and remediation
Result
The trigger notifies the IT Director and escalates the priority of the record when the conditions are met. The action is automated and the entire process is managed through Results – with no external systems or bottlenecks to contend with.
3. Investigate and remediate records
From Results, you can manage the entire remediation process, which includes collecting evidence or input to close out your flagged record and resolve cases. All actions are recorded as a defensible evidence trail to support your investigations.
Example
Scenario
The trigger you recently set up notified the IT Director about three critical records:
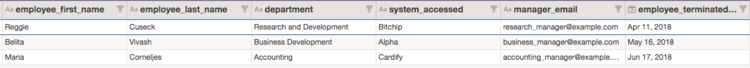
Three employees no longer work for the organization, yet still have access to critical systems. The IT Director must remediate these records by restricting the identified individuals from access to the critical systems.
Process
Help topic Processing records
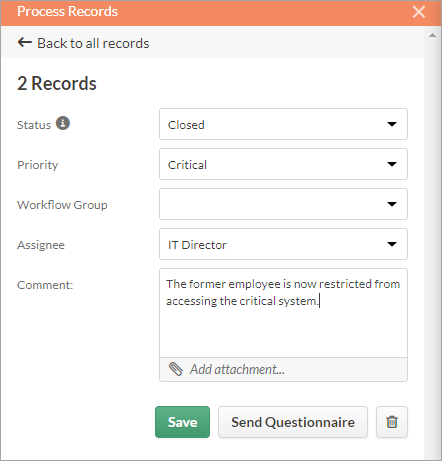
The IT Director performs the necessary work to restrict the individuals from access to the critical systems. After the work is complete, the IT Director adds a comment to the records to confirm that remediation measures have been taken, and closes the records by updating the status field.
Result
Whenever a record is updated, the event is logged in the audit trail of the record (Process View panel > Activity tab). The event includes a description, the user that made the change, and the date and time the change occurred.
4. Report on data
Using the results of attestation projects and incident management root cause analyses, organizations can identify gaps or weaknesses in existing policies and provide feedback to policy writers to develop new policies or strengthen existing ones.
Tip
Policy changes can be populated back into Compliance Maps to begin the new cycle of mapping to regulations. This allows teams to ensure adherence to policy requirements by updating control frameworks, evaluate policy effectiveness through control attestation projects, and manage incidents as they arise.
Visualize data
You can visualize results to gain a deeper understanding of the facts and insights hidden in the data. Storyboards provide a macro view over a larger collection of similar incidents in order to determine trends and analyze the root cause of systemic issues. For frequently recurring incidents, storyboards can be used to report on the incidents portfolio as a whole.
Example
Scenario
You want to visualize and present your findings of your investigative work. By visualizing data, you hope to identify gaps or weaknesses in existing business processes, and provide feedback to the relevant stakeholders to develop new business processes, or strengthen existing ones.
Process
Help topics
First, you create a filtered table that displays the three critical records identified via trigger. Then, you create visualizations that showcase the critical systems accessed by department, and the number of employees within each department that accessed the critical systems. Finally, you create a storyboard to present your findings in a meaningful way to the relevant stakeholders.
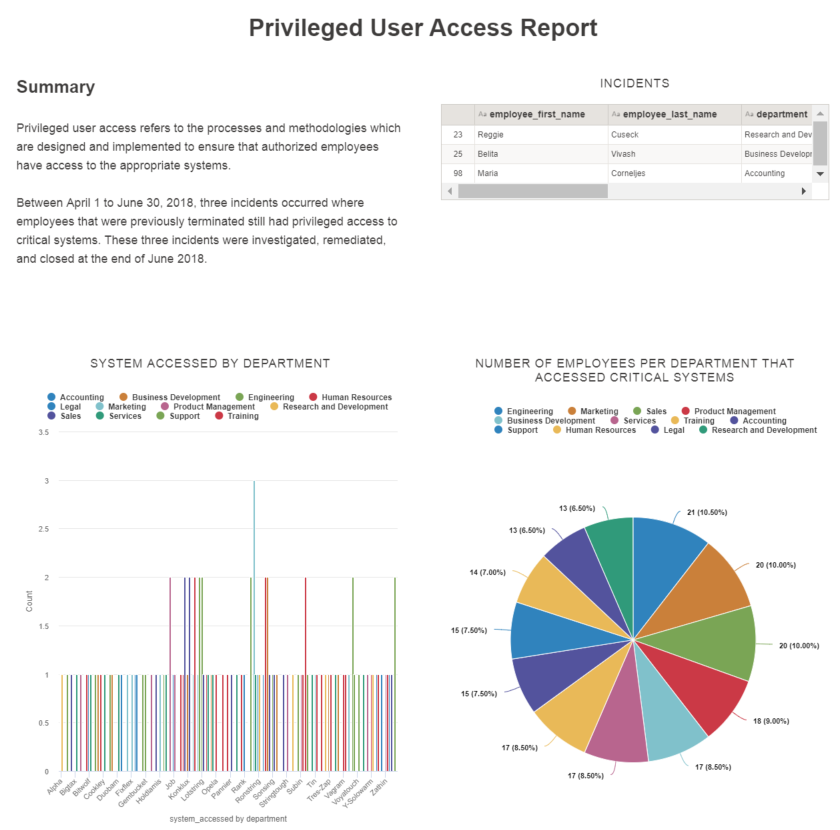
Result
The storyboard displays multiple visualizations and text content in a single, communication platform. Managers and other stakeholders can use this information to detect patterns or trends, analyze the root cause of system issues, and develop more efficient and effective business processes.
For example, one recommendation for a more efficient business process may be to set up a privileged user access request form, so that employees can request access to critical systems – and this is something that you can achieve using questionnaire functionality in Results.
Link Results data to your assessments in Projects
During any assessment phase, you can link Results data to support your documentation in Projects. By linking Results data, you can highlight exceptions or important information that pertains to a control failure, and eliminate subjectivity in risk assessments.
Example
Scenario
As an Auditor conducting work as part of the compliance review process, you need to report on exception data that pertains to a logical access control failure. Previously, you noted a failure associated with the following control in the IT General Controls Review project:
LA-008 Access to the databases supporting the production application is restricted to only those individuals that require such access to their database administration job functions.
You also previously created an issue and an action as a follow-up measure:
| Item | Description |
|---|---|
| Issue Unauthorized employees may have access to critical systems |
There is no process in place to ensure that only authorized employees have access to critical systems. |
| Action Monitor privileged access to critical systems on a regular basis |
Monitor production access logs and compare logged events with a sanctioned user list. |
Process
Help topic Linking evidence from Results
In Projects, you navigate to the appropriate control, and link the Results data to support your documentation:
Result
The Results data is consolidated and linked to your Projects documentation. Now, you can easily review the exception data, and validate whether or not the issue has been truly remediated. The evidence suggests that the organization is beginning to implement measures to monitor privileged access to critical systems in order to comply with the COBIT® 5 Framework.
What's next?
Learn how to demonstrate assurance over a compliance program
The Projects, Frameworks, and Compliance Maps apps can be used to build out attestation projects, capture and assign issues for remediation throughout the compliance review process, report on the effectiveness of controls, and validate and document compliance.
To find out more, see Demonstrating compliance.